Pikabot Malware Attack Demo
Protect your network from Pikabot vulnerability with Juniper Connected Security
This episode of the Juniper Threat Labs Attack Demo series shares how Juniper Connected Security secures your network from the Pikabot malware threat. Explore this vulnerability’s attack’s origins and learn how Juniper SRX Series Firewall and Juniper Advance Threat Prevention (ATP) advanced security services leverage AI to proactively stop threats before they impact your network.
For more information about Juniper Threat Labs, visit: https://threatlabs.juniper.net/home/#/
You’ll learn
How the Pikabot malware infiltrates and impacts infected organizations
How to protect against this threat with Juniper’s SRX firewall and ATP cloud-based anti-malware solution
Who is this for?
Transcript
0:00 welcome to the Juniper threat Labs
0:01 attack demo series for this demo we will
0:05 be talking about peabot malware this
0:08 video will demonstrate how this malware
0:10 emerged in relation to a well-known
0:12 malware recently disrupted by
0:14 FBI afterwards we'll show you how
0:16 Juniper Network's customers can be
0:18 protected to give a background this
0:20 August of 2023 the FBI announced a
0:23 coordinated law enforcement effort code
0:26 named Operation duck hunt that disrupted
0:29 quac bot the operation involved
0:31 collaboration between law enforcement
0:33 agencies from France Germany lvia
0:36 Romania the Netherlands the UK and the
0:40 US the FBI neutralized this far-reaching
0:43 criminal supply chain cutting it off at
0:46 the knees as part of the operation the
0:49 FBI gained lawful access to Boo's
0:52 infrastructure and identified over
0:54 700,000 infected computers worldwide
0:58 including more than 200,000 ,000 in the
1:00 US to disrupt the botn net the FBI
1:04 redirected cckb but traffic to Bureau
1:06 controlled servers that instructed
1:09 infected computers to download an
1:10 uninstaller file the US justice
1:13 department announced that the malware is
1:15 being removed from victim computers to
1:17 prevent further harm and more than $8.6
1:20 million in cryptocurrency was seized as
1:23 illicit profits the takedown did not
1:25 result in any announced arrests cckb
1:28 also known as cubot initially started as
1:30 a banking Trojan in 2007 but evolved
1:33 into a versatile tool for Distributing
1:36 malicious code including ransomware
1:39 major ransomware families propagated
1:41 through kbot include kti prolok egregor
1:45 r evil Mega cortex and black Basta
1:48 following the takedown cockp has
1:50 remained dormant however different cyber
1:53 security researchers noticed an increase
1:55 activity of two malware which share
1:57 similar Behavior with first is the
2:00 darkgate malware and the other one is
2:02 peabot which we will talk about in this
2:04 video peabot is a malicious back door
2:07 that has been active since early
2:09 2023 it initially arrives as a fishing
2:12 email using hijacked email threads
2:15 enhancing the likelihood of the target
2:17 clicking on embedded malicious links the
2:20 emails were believed to be likely stolen
2:22 in an earlier campaign that targeted the
2:24 proxy log and flaw in vulnerable
2:26 Microsoft Exchange servers peabot
2:29 Implement an extensive anti-analysis and
2:31 anti- sandbox techniques to thwart
2:34 automated analysis in sandbox
2:36 environments pick abot communicates with
2:39 its command and control server it
2:41 includes commands to execute shell
2:43 commands download and execute XE dll and
2:47 Shell Code terminate current process and
2:50 collect host information such as
2:51 processes IP information and user
2:54 information in most of its campaigns
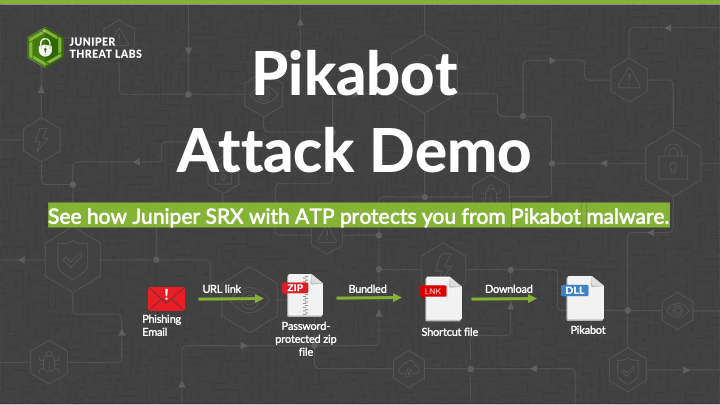
2:56 fishing emails feature malicious links
2:59 that Direct direct users to a password
3:01 protected zip file containing either a
3:03 Windows shortcut file JavaScript or HTA
3:07 file executing these files leads to the
3:09 peabot malware let's start the attack
3:12 simulation in this scenario we have a
3:15 compromised email thread featuring a
3:17 link and a password when the target user
3:20 clicks on the link it triggers the
3:22 opening of a browser initiating the
3:24 download of an archive file named yu.
3:27 zip upon examining the contents of the
3:30 zip file we find a file named tzz pdf.
3:35 lnk it's crucial to observe the double
3:37 extension a deceptive tactic aimed at
3:40 tricking the user into believing it's a
3:42 PDF file let's extract the shortcut file
3:45 and inspect its
3:47 contents in the windows environment
3:50 shortcut files don't merely serve as
3:52 shortcuts to Applications they can also
3:55 include command line
3:56 arguments this feature provides users
3:59 with the flexibility to customize how
4:01 applications or files are
4:04 executed in the context of this
4:06 situation the shortcut file may contain
4:09 system commands allowing the execution
4:11 of multiple commands sequentially
4:14 separated by
4:15 semicolons this includes potentially
4:17 malicious commands like Ping curl and
4:20 rundll32.exe
4:27 upon executing the shortcut file we
4:30 initiate a process monitor to gain
4:32 visibility into what is happening in the
4:34 background we observe the Ping process
4:36 running followed by the rundll32.exe
4:51 [Music]
4:54 process further examination of the
4:57 rundll32.exe process reveals a
4:59 suspicious ul. log loaded as a
5:03 module this ul. log was downloaded as
5:06 part of the shortcut file command line
5:09 it is in fact a dll file as we can see
5:12 its imports and exports let's now look
5:14 and see whether or not this attack works
5:16 as successfully with a juniper SRX
5:18 firewall enhanced with protection from
5:20 Juniper's cloud-based Advanced
5:22 anti-malware solution Juniper
5:25 ATP for the demo Juniper threat Labs is
5:28 using the foll ing setup we have a vsrx
5:31 pictured in the
5:33 center the vsrx is a virtual SRX
5:36 firewall providing network security
5:38 protection its purpose is to inspect
5:41 Network traffic and with the assistance
5:43 of juniper ATP Cloud to detect malware
5:47 in addition to the virtual firewall and
5:49 cloud-based protections we are using
5:51 Juniper security director which is a
5:53 centralized management system it is used
5:56 to facilitate our configuring and
5:58 monitoring of the VSR RX firewall and we
6:01 are using Juniper's policy enforcer as
6:04 well Juniper's policy enforcer enforces
6:08 security policies on end points and
6:10 ensures they comply with corporate
6:12 security
6:14 standards we also have several Windows
6:16 workstations Each of which is connected
6:19 to the
6:21 vsrx finally we have an Ubuntu Server
6:24 acting as the malware download server
6:26 before we proceed an attempt to simulate
6:28 this attack with Jun connected Security
6:30 Solutions in place providing protection
6:33 let's first take a look at the threat
6:34 prevention policy that we've set up on
6:37 our security director and appli to the
6:40 vsrx to access the policy we'll navigate
6:43 to the configure Tab and then we select
6:46 threat prevention and
6:49 policies as you can see we already have
6:51 an existing policy in place let's
6:54 further inspect the protections being
6:56 enforced by the applied
6:57 policy for this demo our policies are
7:01 configured to block command and control
7:03 traffic at Threat Level 8 and
7:05 above we've also set it up to block
7:08 infected hosts at Threat Level 8 and
7:11 above additionally we've configured our
7:14 policy to use ATP cloud from malware
7:17 detection and as you can see we've
7:20 elected to scan HTTP downloads and block
7:23 threats at level seven and
7:25 above this threat prevention policy
7:28 implied to the Juniper V SRX firewall is
7:30 a critical component of our defenses
7:33 protecting our systems against malware
7:35 related attacks it allows us to detect
7:38 and block malicious traffic as well as
7:40 the activity of potentially infected
7:42 hosts which will then prevent the spread
7:45 of malware throughout our Network in the
7:47 event that one of our systems gets
7:48 compromised with that let's proceed with
7:51 the attack using Juniper connected
7:54 security to get started we'll connect to
7:57 our Target system via RDP as you can see
8:00 we have a fishing email with a link
8:02 leading to the malicious archive file
8:04 yu. zip when we click on that it opened
8:08 the browser to download the zip file but
8:11 as you can see the request has been
8:13 blocked due to malware detection we can
8:15 verify this in the security director by
8:17 navigating to
8:19 monitor threat
8:24 prevention HTTP file
8:28 download
8:30 here the file yu. zip is flagged with a
8:33 threat level of 10 according to our
8:35 policy we configured earlier threats
8:38 with Threat Level s and above will be
8:40 blocked we can find more details about
8:43 this file when we clicked on it and it
8:45 gives us more information such as
8:47 Behavior Analysis network activity and
8:50 behavior details including the client IP
8:53 address the SRX device and the URL at
8:56 this point the attack chain is already
8:58 blocked and thus thus the second stage
9:00 cannot proceed but for the purpose of
9:03 showing how SRX can block attacks
9:05 further down the attack chain we copied
9:07 the archive file and extracted the
9:09 shortcut file as you can see we will try
9:12 to execute this shortcut file but you
9:14 will notice that the execution of run
9:16 dll 32. XE fails that is because ul. log
9:21 in this case was successfully blocked by
9:28 SRX
9:29 we can verify that once again in the
9:31 security director here we can see that
9:33 the file with a sha256 hash that starts
9:36 with ABF is flagged at Threat Level 10
9:39 similarly we can also find more
9:41 information about this malware when we
9:43 clicked on it note that while the attack
9:46 was unsuccessful recall that the
9:48 security policy being enforced on the
9:51 vsrx locks host network activity when it
9:54 detects threats at level 8 and above
9:58 when we click on ATP Cloud hosts we can
10:01 see that the IP
10:03 10.0.1 161 is flagged at Threat Level 9
10:07 this Threat Level score is determined by
10:09 multiple factors such as malicious
10:11 activities by that host including
10:13 malware downloads and command and
10:15 control connections this host then is
10:18 now included in the infected hosts feed
10:21 what this means is that this host is now
10:24 isolated and disconnected from the
10:25 network
10:26 temporarily we can confirm that as we
10:29 cannot connect via RDP as
10:37 before clicking at this host provides us
10:39 with more details on why it is
10:42 blocked as shown here the host attempted
10:45 to download two malicious files with
10:47 Threat Level 10 once the admin is sure
10:49 that the host or server is indeed free
10:51 from infection he or she can first
10:53 select the host and then under the
10:55 investigation status section select
10:57 resolved fixed which changes the status
10:59 of this host to clean and exclude this
11:01 host from the infected host's feed after
11:05 a few moments this host will be
11:06 connected back to the network again we
11:09 can verify that once again by connecting
11:12 to it via RDP and browsing the
11:27 net
11:31 that completes our demo of peabot
11:32 malware check out more videos from the
11:35 Juniper threat Labs attack demo series
11:37 by visiting juniper.net thanks for
11:39 watching






























