Configuring Juniper Secure Connect: Security Director

Learning Byte: Providing remote access to server-1 the easy way.
If you are new to working with Juniper Secure Connect and have a small number of users, then this video demo is for you. Follow along as Juniper’s Zach Gibbs walks you through configuring Juniper Secure Connect using Security Director from start to finish. This is part one in a two-part series.
You’ll learn
How to use Security Director to give a small business’s remote worker access to server-1
The first things you need to do in the configuration process involving security devices
How to create the connection from the remote worker’s device through the VPN
Who is this for?
Host

Transcript
0:00 [Music]
0:11 hello
0:12 my name is zach gibbs and i'm a content
0:14 developer within
0:16 education services inside juniper
0:18 networks and today we will be going
0:21 through
0:21 the configuring juniper secure connect
0:24 security director
0:25 part one learning byte okay so here is
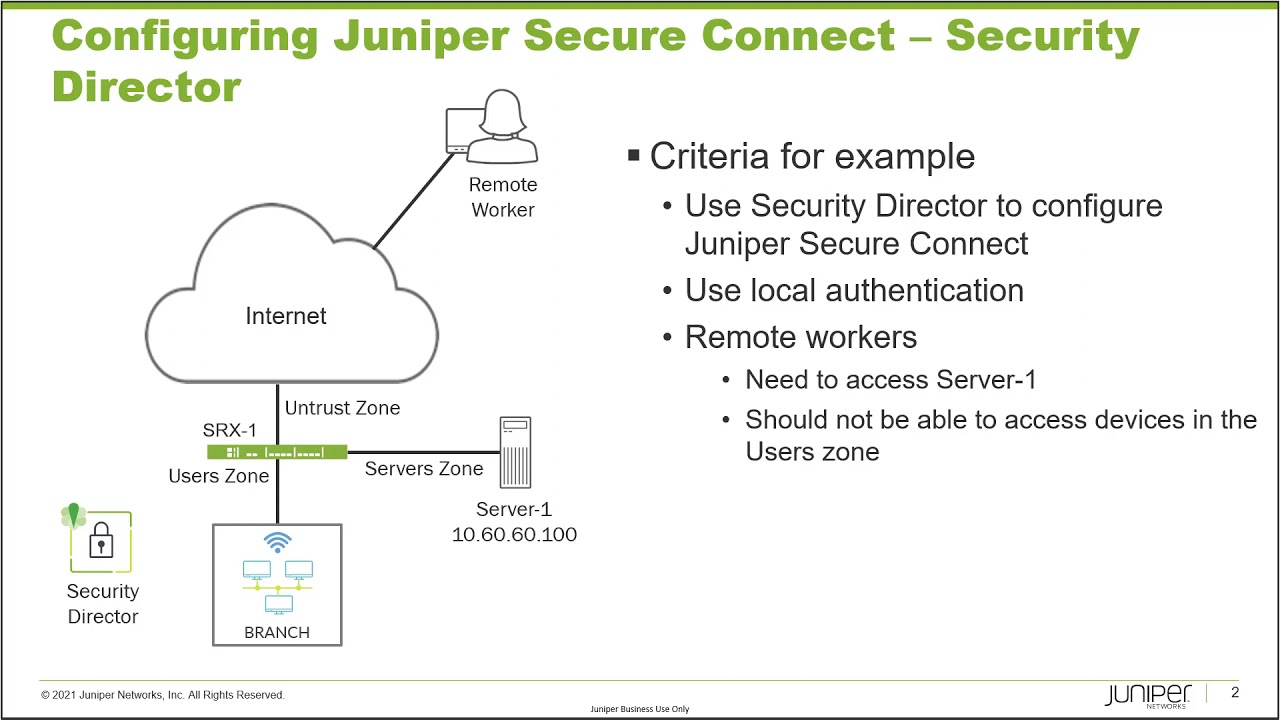
0:28 our example in this example i want to
0:31 first talk about the topology
0:33 and here in the topology you can see a
0:36 couple different devices we have
0:38 srx1 which we will be configuring using
0:41 security director and then srx1 is
0:43 connected to the users in the branch
0:46 which is the user's zone and then we
0:48 have server one which is connected into
0:50 srx through the servers
0:52 zone and then we have the internet which
0:54 connects to the srx1
0:56 using the untrusted zone and so what we
0:59 have here is we have a remote worker who
1:01 needs
1:02 access to server 1 and so
1:05 what we want to do is we want to use
1:07 security director to configure
1:09 juniper secure connect and we're going
1:12 to use
1:12 local authentication and that is good
1:16 for a small business where you don't
1:18 have a lot of workers if you have
1:20 hundreds of people who need
1:21 access remote access that is then you'll
1:24 probably want to use something like
1:25 radius authentication where it'll be a
1:28 lot easier to manage all those users
1:30 and so with that being said we have our
1:33 remote worker who needs access to server
1:35 one and this remote worker should not be
1:37 able to access
1:38 hosts that are in the user zone and so
1:40 with that being said let's go ahead and
1:42 jump to security director
1:44 and get this going all right so here is
1:47 security director and we're currently in
1:49 the configure workspace
1:52 and we'll do some work in here but first
1:53 we need to jump to the devices workspace
1:56 so here is srx1 and the first thing we
1:59 need to do
2:00 is we need to create the local
2:02 certificate that we'll be using
2:04 and to do that there's no real easy way
2:07 in security director
2:08 and so we'll need to use the access
2:11 option to
2:12 launch an ssh session to srx1
2:16 and then login
2:20 and here in srx1 we're going to first
2:23 create
2:23 the key pair that we're going to use
2:28 specify a size of 2048 and then a type
2:33 of rsa and then the certificate id we're
2:36 going to use
2:37 is juniper r a
2:41 lb for learning bytes so remote access
2:44 learning byte
2:45 okay great that's created let's go ahead
2:47 and use that key pair to create a
2:49 certificate
2:53 specify a certificate id of that key
2:56 pair
2:57 and then specify a subject we're going
2:59 to say dc
3:01 equals juniper
3:05 cn equals edl then domain
3:08 of edu.juniper.net
3:11 and then we need to specify an ip
3:13 address and this is very important
3:14 because
3:15 this ip address we'll need to reference
3:18 when creating the remote access vpn
3:20 using juniper secure connect
3:22 click enter to create that certificate
3:24 okay so we're good there so we can close
3:26 that
3:27 and that's the only thing we'll need to
3:28 do in the cli today
3:30 and then we need to do some more device
3:32 configuration we'll go to configuration
3:35 modify configuration okay so we need to
3:37 scroll down to the very bottom here and
3:39 we'll see
3:39 system services we'll expand that
3:43 scroll down some more and we see at the
3:45 very bottom https services that's
3:47 currently not turned on we need to
3:49 select allow to turn that on
3:51 and then if we scroll down we can select
3:52 some interface if we don't select any
3:54 interfaces then it's going to be applied
3:56 to all interfaces
3:57 and by default we have system generated
3:59 certificate we want to change that to
4:00 pki
4:01 local certificate and then select the
4:04 certificate that we just created
4:07 we could specify a different port but we
4:09 need to leave that at the default of 443
4:11 and then the next thing we need to
4:12 configure is we need to configure the
4:14 security zone
4:15 the untrust security zone it's already
4:18 configured here but we need to
4:19 edit it and add in some system services
4:24 and if we scroll down we have system
4:26 services
4:28 oh wait a little too far https
4:32 is necessary and then
4:35 tcp encapsulation
4:40 and then ike
4:45 then we can click okay and then we can
4:48 preview changes to
4:50 kind of see what we're doing here and
4:52 you can see here it's pretty
4:52 straightforward we're adding https ike
4:55 and tcp and cap to the untrust
4:57 zone for host inbound traffic and then
5:00 we
5:01 are setting the web management https
5:04 certificate to the juniper ra-lb that
5:07 certificate we just created a few
5:09 moments ago
5:10 so close that and click save and deploy
5:13 and that will just take a second
5:14 after we click ok again to run it and
5:16 great
5:17 that job went through successfully let's
5:19 go ahead and click ok
5:20 now we can jump back to configuration
5:22 mode
5:25 and we're going to need to create a few
5:26 things let's go ahead and start with the
5:29 firewall policy that we'll need
5:30 so let's create a new policy we'll call
5:33 this
5:34 ra fw
5:37 all for short for policy and then we'll
5:39 move s or x1 over
5:43 and then we need to create some firewall
5:45 rules
5:46 for this policy so we'll call this
5:50 from remote
5:54 workers and then the source address
5:57 or the source information is going to be
5:59 vpn it'll be coming into the vpn
6:01 zone and then it'll be going to the
6:04 servers
6:05 zone and here let's go ahead and select
6:08 an address
6:09 we'll select and add the server
6:13 address here and granted that to say
6:16 server one two three it's actually
6:18 server one
6:19 sdip address the server one i meant to
6:21 change that earlier but here we have it
6:23 click ok then we'll select permit
6:27 under advanced security and we could add
6:28 different parameters here such as ips or
6:31 app firewall if we
6:32 wanted to scan this traffic or idp
6:35 threat prevention things like that
6:37 and then let's go ahead and jump to the
6:39 end and finish off this rule
6:43 and then we need to create a rule for
6:46 the server
6:48 so we'll say to
6:51 remote worker
6:54 so source address this will be coming
6:56 from the servers zone
6:58 and we're going to select that server
7:00 address
7:07 and then in the destination information
7:09 we're going to select the
7:11 vpn zone and then of course permit the
7:13 traffic and you could add additional
7:15 security
7:16 checks here if you wanted to of course
7:19 and then
7:20 rule placement let's click finish click
7:23 ok
7:24 and so things look pretty good there
7:25 we'll go ahead and save that
7:27 and we'll publish it but we won't update
7:29 the devices yet because we can do a
7:31 publish
7:32 now and then an update later once we
7:34 have everything else configured that
7:35 we're doing for this learning byte
7:37 and great you can see that went through
7:39 successfully that job no problems there
7:42 so let's go ahead and move on to the net
7:45 configuration
7:46 so we'll go to nap policy policies
7:50 and let's create a new nap policy and
7:52 i'll explain why we're doing this
7:54 because there's a specific reason
7:55 to do this
7:59 give it a name select srx1
8:04 and then let's create a new rule here
8:11 create a source rule and then the source
8:14 ingress information we're going to say
8:17 from zone
8:18 vpn and
8:21 source address we're just going to put
8:24 down any ipv4 address
8:26 so match on everything coming in from
8:28 the vpn zone
8:30 and you could specify more specific
8:32 information here if you would like
8:34 and then destination egress
8:37 we're going to specify the servers zone
8:41 and then we're going to specify
8:43 translation
8:45 of interface so it's going to be the
8:47 source interface
8:50 and what we're doing here let me explain
8:52 the reason behind this so traffic is
8:54 going to be coming in from the
8:55 vpn zone and we haven't done it and
8:58 we'll do this in the next learning byte
9:00 that is the second part of this learning
9:02 byte but
9:04 we will have to assign the remote worker
9:06 a certain ip address
9:08 and the server won't know how to get to
9:10 that ip address or rather it'll think
9:12 it'll need to use the default route to
9:14 get to that ip address
9:16 and so if it does that it'll send the
9:17 traffic to the srx the srx will think it
9:20 needs to use a default route and then
9:21 send the traffic out
9:22 its internet-facing interface without
9:24 putting the traffic in the tunnel
9:26 so we can get around this problem by
9:28 doing a source
9:30 nat on the traffic coming in from the
9:32 vpn going towards
9:34 the server because what happens is we
9:36 are doing
9:37 source net on that interface that is
9:39 pointing towards
9:40 the server one device and so what
9:43 happens
9:44 is that traffic comes in the source net
9:46 changes it to the ip address which in
9:48 this case is 10.60.60.254
9:52 then the server being 10.60.60.100
9:55 knows that it just sends it to the
9:58 10.60.60.254 address
9:59 and when that happens reverse sourcenet
10:02 will take the traffic and then
10:04 change the ap address which then gets it
10:06 into the tunnel and so this allows the
10:07 routing to happen
10:09 as needed and so what we could do
10:12 besides this is we could use some sort
10:14 of static routing
10:15 to put the return traffic back inside
10:17 the tunnel so let's go ahead and publish
10:20 this
10:22 and then we'll move on after that and
10:24 that job is complete so let's go ahead
10:26 and close that window
10:27 and then let's go ahead and go back to
10:30 devices
10:34 and then we'll do an update and we'll
10:36 update those two changes
10:38 for firewall policy and nat to srx1
10:43 and those firewall policies and nap
10:45 policy were successfully pushed to
10:47 srx1
10:53 and so quickly let's look at the
10:54 topology as a reminder we have srx1
10:57 which has three different interfaces we
11:00 have
11:00 the user's zone connection the server's
11:03 zone connection
11:04 and the untrust zone connection and the
11:06 user zone
11:07 houses the users in the branch and the
11:09 server zone houses server one
11:12 and the untrust zone connects to the
11:13 internet and we have the remote worker
11:16 who needs to connect in
11:17 to srx1 into this site and then
11:21 they need to be able to access server
11:23 one now
11:24 with that the remote worker should not
11:26 be able to access
11:27 anything in the user zone but owens
11:30 should be able to access
11:31 server one and so we're using security
11:33 director to configure this
11:35 and we're using local authentication and
11:37 so with that
11:38 let's go ahead and jump to security
11:41 director to finish this learning byte
11:42 series
11:45 okay so here is security director recall
11:47 from the last learning byte
11:49 that we created the local certificate
11:52 we configured the srx1 device to use
11:55 that local certificate and then we
11:57 created some firewall policies as well
11:59 as a source
12:00 nat policy so next let's go to configure
12:03 workspace and then go to ipsec vpn
12:07 ipsec vpns and then create vpn
12:11 route-based vpn and then remote access
12:14 juniper secure connect and here we can
12:17 name the vpn
12:20 then we can give a description that's
12:21 not necessary we have to use the traffic
12:23 selector
12:24 auto route insertion option and we'll
12:26 see how that's configured
12:27 we can specify a vpn profile but using
12:29 the default works well
12:31 and then the method for what we need to
12:33 use is pre-shared key since we're using
12:34 local authentication
12:36 and the pressure key we can either
12:38 define one or we can just auto generate
12:40 it and auto generation is perfectly fine
12:42 for here
12:43 and we can use the generate a unique key
12:46 per tunnel as well and that's set to on
12:48 and then to begin we need to click the
12:50 remote user icon
12:52 and that starts us off with asking us
12:55 which device we want this to be for and
12:57 we just have s or x1 here typically when
12:59 using security directory you'd have a
13:01 lot more than srx1
13:03 but since this is a learning byte that's
13:04 all we need to do
13:06 we click ok there and then we have the
13:08 remote user configuration
13:10 again we are using the default profile
13:12 connection mode is set to manual
13:13 we can have it set to always but manual
13:15 works fine for what we're doing
13:16 ssl vpn we want to leave that on we have
13:19 dead pair detection configured as well
13:21 by default and windows login is
13:23 not selected as well as biometric
13:25 authentication both of those
13:26 can be configured for a remote access
13:28 vpn with juniper secure connect
13:32 we'll click ok then the next thing we
13:34 need to do is select the
13:35 srx1 device to configure the rest of it
13:38 external interface that's going to be
13:40 gigi001 and notice how the 10.111.111.1
13:45 ip address is associated with that
13:47 remember that in the previous learning
13:48 byte we referenced that ip address
13:51 when creating the certificate the tunnel
13:54 zone in our case is going to be vpn now
13:56 i created that zone beforehand and then
13:59 user authentication there's nothing to
14:00 select here so let's go ahead and add
14:02 some user authentication
14:03 and notice here up top this is very
14:05 important says update access profile
14:07 before updating remote
14:08 vpn now when i first tried to do this i
14:11 didn't see that
14:12 and things didn't work out i tried to
14:14 push the configuration and it
14:16 failed and that's because after we
14:18 create the vpn before we send it to the
14:20 device we need to go to the remote
14:21 access configuration
14:23 and update that first so keep that in
14:25 mind that's incredibly important
14:31 i set this to local and of course
14:35 there's nothing
14:35 for address assignment yet so we need to
14:37 create an address pool
14:39 and we'll call this poll r a dash full
14:42 dash
14:42 sd lb and then we need to specify the
14:46 network address
14:47 we'll use that 10.77.77.0
14:50 make that a 24. and then we need to
14:53 specify a
14:55 dns server that the user can use and
14:58 then let's go ahead and specify an
14:59 address range that can be used within
15:01 that pool first we need to call it
15:03 we'll call this ra pull sd
15:06 lb and we'll set the lower limit to
15:09 10.77.77.10 so we're going to start
15:11 handing out
15:12 ips with that address then a high limit
15:14 of 10.77.77.50
15:18 go ahead and click the checkbox and
15:19 click ok and then we need to add a local
15:22 user
15:25 lab lab123 pretty standard for education
15:28 services there
15:29 and then we're done with the address
15:31 assignment
15:32 part and the user authentication now we
15:35 need to
15:36 use an ssl vpn profile there's nothing
15:39 here so we do need to add one
15:42 and we'll call this a cell vpn sd-lb for
15:46 the profile name
15:48 and we need to create an ssl termination
15:51 profile
15:52 and this is something that we're just
15:53 going to name here and the system will
15:55 create the actual profile for us because
15:57 what happens with this profile
15:58 is the termination profile that is is
16:01 that we name it and then we reference
16:03 the certificate then we reference that
16:08 certificate that we created in the
16:10 previous learning byte
16:12 and click ok and we're not quite done
16:14 yet we have to specify a protected
16:16 network
16:17 now here we have an address of server
16:20 123 which is actually server one i meant
16:22 to change that before
16:23 did these learning bytes but that's the
16:25 ip address associated with server one
16:27 and that works great and when we do this
16:29 this automatically
16:30 will create a scenario where split
16:32 tunneling happens meaning
16:34 only traffic to the server is going to
16:35 go through the tunnel for the remote
16:37 worker
16:38 and all other traffic will use the
16:40 remote workers normal internet
16:42 connection
16:43 and that's exactly what we want now if
16:44 we didn't want that we'd have to specify
16:47 an address that is a default
16:50 address so all zeros so 0.0.0
16:53 0 and that would cause all the traffic
16:56 to go through the tunnel
16:57 because we would consider everything to
16:59 be protected networks
17:01 and so that means we would send
17:02 everything through the tunnel now you
17:04 can do that if you want
17:05 but in our case we don't want to do that
17:06 and that's very applicable right now in
17:08 today's world where we have a lot of
17:09 remote workers
17:11 if you're sending all of their traffic
17:12 through the srx device for
17:14 all your remote workers that might
17:16 overwhelm your srx device
17:18 so let's avoid that and just send the
17:20 traffic through the tunnel that we need
17:22 to send
17:23 okay so that almost finishes the
17:25 configuration we need to scroll down
17:27 under ike and ipsec settings and this is
17:30 going to be under ike you need to
17:32 specify an email address and i actually
17:34 changed that keep a live i believe it
17:35 was at 10 so we'll change that back
17:38 and we're going to say lab
17:42 edu.juniper.net
17:43 and that's going to be a part of the ike
17:45 id
17:46 and so we go up here and click save and
17:48 then we'll have one more thing it'll
17:49 prompt us for
17:50 it'll say new profile name what this is
17:52 is this is the dynamic configuration in
17:54 the cli
17:56 and so we'll need to specify the name
17:57 and then we'll need to
17:59 set it to shared as well so we'll set
18:01 this as ri-dine-sd-lb for the name and
18:05 we'll set it to
18:06 shared and we've completed that
18:10 configuration but remember we need to
18:12 jump to the axis configuration before we
18:14 push this vpn configuration to srx1
18:17 so that is going to be under user
18:18 firewall management
18:20 and then access profile and you'll see
18:23 this is that access profile we created
18:25 so we can select that and click update
18:28 and that will push it out to
18:29 srx1 you just select srx1 click
18:32 update confirm it and let's go ahead and
18:35 click on the job
18:36 number and we'll see great that worked
18:38 out 100
18:40 successful state so we're good there so
18:42 let's go ahead and jump back to
18:43 configure
18:45 and then go to ipsec vpn and ipsec vpns
18:50 and then select our remote access
18:52 juniper secure connect vpn
18:55 and click update and we'll click publish
18:58 and
18:58 update confirm it
19:02 all right so that job completed
19:04 successfully that's great
19:05 so let's go ahead and jump to the remote
19:08 worker device
19:08 and see how this works
19:12 okay so here is the remote worker device
19:15 and first i want to show that we
19:16 actually can't
19:17 reach that server server one from
19:20 the remote worker device if we're not
19:22 connected through the vpn and that's
19:23 perfect that's what we want to see if
19:25 this wasn't the case then this would
19:26 mean that anybody on the internet could
19:28 reach it
19:29 so that's great well with that let's go
19:32 ahead and use juniper secure connect
19:33 that i have right here
19:34 and you can see i've already created a
19:36 profile for something else let's create
19:38 a new connection
19:39 and with this notice that it
19:41 auto-populated the gateway address
19:43 now if this was your first time using
19:45 juniper secure connect
19:47 you would need to type this in and so
19:48 we've typed in this information
19:50 and let's click the connection button
19:53 and we're prompted for our user id and
19:55 password
20:00 and then we're presented with a
20:01 certificate warning now why are we
20:03 presented with this well the reason is
20:05 this is the local certificate that we
20:07 create
20:08 this is not going to be a trusted
20:09 certificate by default because
20:11 we created it not a trusted certificate
20:14 authority
20:15 so we can just accept this and you can
20:18 see here i want to show that vip address
20:20 is a part of this certificate that's
20:21 very important
20:22 so let's click accept
20:25 and then the vpn is starting to
20:27 establish
20:30 and the connection is successful great
20:33 and look at the side here we can see
20:35 that the
20:36 communication is occurring like it
20:38 should we can
20:39 reach server 1 using its ip address
20:42 and so perfect that's what we want to
20:44 see now something else i do want to show
20:46 is since we are doing split tunneling
20:48 you can look at the data here you can
20:50 see that we've sent
20:51 some data receive some data there's one
20:53 one three or one one one three
20:55 and one one one three and so what
20:57 happens if we send something to an
20:59 internet
21:01 address like the google dns server
21:05 and notice how that doesn't increment
21:08 those
21:08 we're still at the same numbers that we
21:10 were before and that's perfect that's
21:12 what we want to see
21:17 and it doesn't go through the tunnel
21:18 because we configured it that way
21:20 and so if we were to ping the server
21:22 again you can see
21:24 that the data transmit kilobytes and
21:26 data received
21:27 in kilobytes is incrementing and that's
21:29 perfect that's exactly what we want to
21:31 see
21:33 so that brings us to the end of this
21:34 learning byte in this learning byte we
21:36 demonstrated how to configure and verify
21:38 juniper secure connect using security
21:41 director so as always
21:42 thanks for watching visit the juniper
21:46 education services website
21:48 to learn more about courses view our
21:51 full range of classroom
21:52 online and e-learning courses
21:55 learning paths industry segment and
21:58 technology specific
22:00 training paths juniper networks
22:02 certification program
22:04 the ultimate demonstration of your
22:06 competence and
22:07 the training community from forums to
22:10 social media
22:11 join the discussion