Configuring a Mid-Size Campus
Configure a mid-size campus network.
Learn how Wired Assurance configures a pair of collapsed campus core switches (EX4650 Ethernet Switches), access switches, and connected devices (APs, IoT, and users). See firsthand how all the elements come together in this Wired Assurance demo.
You’ll learn
Creating switch templates
Configuring port profiles
Switch port mapping
Who is this for?
Transcript
0:00 hi everyone welcome to the next video in
0:01 the wide assurance series
0:03 what we wanted to show you now is a
0:05 worked example of how to actually put
0:07 together all the elements that have
0:08 previously been demonstrated
0:11 if you refer to the on-screen diagram
0:13 what we're going to now configure using
0:14 wide assurance is a
0:16 pair of collapsed core switches these
0:18 are ex4650s
0:20 and a set of access switches and i'm
0:23 going to use an example of both a
0:24 virtual chassis stack and a
0:26 standalone ex switch okay let's get
0:29 going
0:30 first off let's dive into creating a
0:32 switch template you can do that by going
0:34 into the
0:35 the organization part of the menu and
0:36 then clicking on switch templates
0:38 i've actually already got a template
0:39 ready that i want to show you so i'm
0:40 just going to click straight in here
0:42 first off let's give this template a
0:43 name here you can see just called the
0:45 campus template
0:47 templates are actually broken down into
0:49 three sections by which you can
0:51 apply configuration to all switches
0:53 shared between switches and
0:54 only to individual switches let's start
0:57 though on all switches
0:58 first off i'm going to set my radius
0:59 server ip addresses
1:01 along with the timeout values i also
1:04 have an
1:05 ntp server which i set here finally in
1:08 the cli configuration box
1:10 include any common elements of
1:12 configuration that you need to apply to
1:13 all switches
1:14 the next step in the template
1:16 configuration is to define
1:18 the networks and part profiles so first
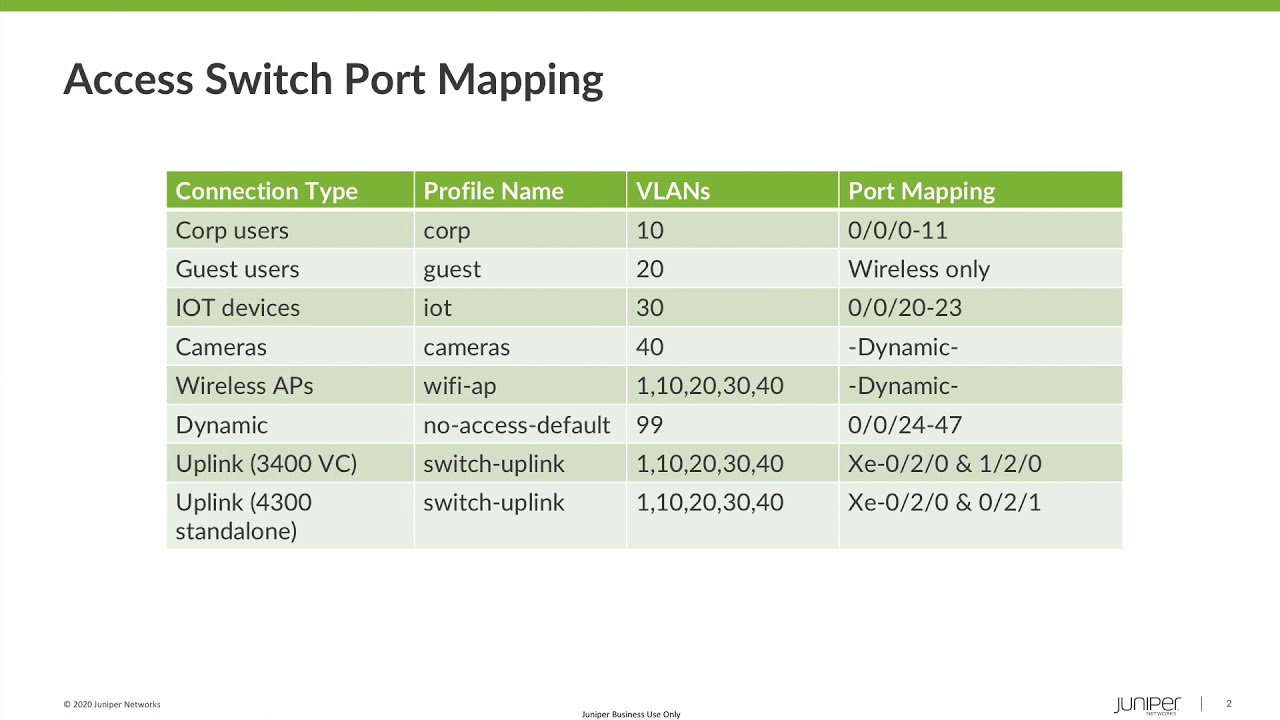
1:20 just looking quickly at this slide
1:22 these are the vlans that i'm going to
1:24 define in the in the network
1:26 section we we basically have a vlan for
1:29 each of the service types so we have our
1:31 corporate users guest users iot devices
1:33 and cameras
1:34 we also use a default vlan for in-band
1:36 management
1:37 and we have a special vlan which i'm
1:39 numbering as 99 as a restricted use vlan
1:42 which we'll use for the dynamic port
1:44 profile configuration
1:46 with the dynamic port profile
1:47 configuration the the vlan 99 will
1:49 effectively mean that
1:50 the traffic has no router anywhere
1:52 unless then the switch detects through
1:54 the dynamic
1:55 profile configuration a specific device
1:57 that then can be remapped to a specific
1:59 vlan for example
2:00 a wireless access point or camera or iot
2:04 device
2:05 okay so going back to the portal if we
2:06 go into shared elements
2:08 and we look at the network section this
2:10 is where we define the the vlans that i
2:12 listed
2:13 in the slide you just need to click the
2:15 add network button
2:16 enter name the vlan id okay now let's
2:19 define some port profiles just referring
2:20 to a slide for a moment
2:22 what we have here are eight different
2:24 profiles
2:25 each which define a mapping between the
2:27 relevant vlans
2:28 and the type of part on the switch okay
2:31 back to the
2:32 missed portal looking at the part
2:33 profile section fairly simple to add
2:35 just click add profile
2:37 you need to give it a name and then we
2:38 can set the parameters for the kind of
2:40 part that we're describing so whether
2:41 it's trunk part or an access part
2:42 the associated vlans whether it's a
2:45 voice part
2:46 for a trunk port you can actually set
2:48 the untagged or native vlan
2:52 and then down here you can actually tag
2:53 in either all networks or specific
2:56 specific networks that you want to
2:57 remember of the trunk then you have all
2:58 the parameters like speed duplex whether
3:00 it's poe port
3:01 let's have a quick look at a profile
3:03 i've already defined this is one for the
3:04 cameras so this is an access port i'm
3:06 adding it to the camera vlan
3:07 and there are no other special
3:08 parameters to set for this one
3:11 and now if i look at my switch uplink
3:13 part this is actually going to be
3:14 defined as a trunk
3:15 i'm using vlan 1 as the untagged and
3:18 then tagging in all of the defined vlans
3:20 that i require the no access profile is
3:23 specifically for
3:25 using with the dynamic port
3:26 configuration so this one sets
3:28 the vlan to the no access vlan as the
3:30 default for that part
3:32 and now let's build the logic to
3:33 actually build that dynamic port
3:34 configuration let's have a look at my
3:36 existing rule here
3:37 what i'm actually going to do is match
3:38 on the lrdp chassis id which is
3:40 basically the mac address and then apply
3:41 the configuration profile of wi-fi ap
3:43 with this then as soon as the switch
3:44 detects a new connection
3:46 matching that mac address string this
3:47 switch will then dynamically apply a new
3:49 profile
3:50 the next step is to look at the select
3:51 switches configuration for the different
3:53 switch types that we have in topology
3:55 before we do that a quick reference of
3:57 the part mappings for what we're going
3:58 to do
3:59 on the distribution switch the
4:01 distribution switch is actually virtual
4:02 chassis so we've actually got the
4:04 members zero and one we're going to
4:06 configure parts four five and six on
4:08 both members to face towards the access
4:09 switch
4:10 i'm going to use part zero on both
4:11 members to face the one router in this
4:13 case it's an srx
4:15 okay if we hop back into the ui and
4:17 select switches configuration
4:20 the first step would actually be to
4:21 click add rule but i've actually got
4:22 some set up here but what you do is you
4:24 give it a name
4:25 and you define a role that you want to
4:26 apply it to you then define
4:28 each of your parts and the profiles to
4:30 those ports
4:31 let's have a look at how these are
4:33 configured so you specify the
4:35 port range that you wish to apply the
4:37 configuration profile to
4:38 and as these are actually going to be
4:40 lag interfaces in most cases you tick
4:42 the part aggregation box
4:45 if you need to include any special
4:46 configuration for that device type go
4:47 into cli config and you can paste that
4:49 in here
4:51 okay so that's the select configuration
4:53 complete for the distribution switch
4:54 let's look at the access switches
4:57 let's just have a quick review of the
4:59 part mappings again for the access
5:00 switches
5:01 what we're looking to do here is to
5:02 simply pre-define some port ranges that
5:04 can be applied across all switches so
5:05 that the rollout is highly templatized
5:07 therefore any new switch is added into
5:09 the environment later we'll just simply
5:10 inherit the same configuration
5:12 for my topology i'm going to create two
5:13 more select switch configuration
5:14 profiles
5:15 here i've got my standalone switch
5:16 configuration profile defining my port
5:18 ranges
5:19 to power profile mappings
5:22 and now for my two member virtual
5:24 chassis same again
5:26 as all the other switches define the
5:27 port ranges mapping those to the
5:29 configuration profiles
5:31 on the switch up links specifically do
5:33 remember to tick the
5:34 port aggregation box so these will be
5:35 lags facing the distribution layer and
5:38 for the parts that we want to apply
5:39 dynamic configuration to ensure to tick
5:42 the enable dynamic configuration box
5:43 this thing will pull in the
5:44 configuration previously applied where
5:46 we
5:46 match on the mac address okay great so
5:50 that's our campus template finished
5:51 remember to click
5:52 save when you're done at the end of this
5:53 stage what we need to do now is actually
5:55 on board the switches
5:57 so if we navigate into organization and
5:59 inventory
6:00 then to switches as we're using a
6:02 brownfield method here we're going to
6:04 use the adopt switches process
6:06 simply copy the adoption text and paste
6:09 it into your terminal on the switch
6:10 the device will then begin to onboard in
6:12 the background after you've done a
6:13 commit
6:14 your switch will then appear in the
6:15 inventory list with a grey icon i'm
6:17 using an existing switch here what you
6:18 do is you need to tick the box and then
6:20 click assign to site
6:21 i'm assuming you've already got a site
6:22 created but if not navigate to
6:24 organization and sites
6:25 you can click create sites and define
6:27 all the parameters in here
6:29 okay carrying on with the onboarding
6:30 let's work on the distribution switch
6:32 first
6:33 make sure we set a hostname but then
6:35 let's actually look what happens
6:37 with inheriting comfort from the
6:38 template so without the role specified
6:40 we don't pull in
6:41 any of the select switches configuration
6:45 if you type in the role name l2 disk
6:46 here like we defined in the template
6:48 the switch then inherits all the
6:49 configuration for the parts
6:51 and any other rule-based cli commands
6:54 that were in the additional settings
6:55 within the select switches configuration
6:57 now let's look at the other
6:58 configuration elements pulled through
6:59 from the template first we're inheriting
7:00 the dynamic port configuration
7:02 the part profiles and all the vlans
7:06 main point stress here is that you've
7:07 not had to do any of this manually it's
7:09 all been inherited from the predefined
7:10 template
7:12 okay this which is done it's inherited
7:13 all the config we need let's click save
7:16 all we now need to do is repeat the same
7:17 workflow for the access switches just
7:19 taking a quick walkthrough of each
7:20 switch then
7:21 make sure you apply the name and a roll
7:23 so that the switch inherits all of its
7:24 necessary configuration
7:29 despite fully on board let's look at
7:31 some of the in life management features
7:32 let's go into the
7:33 topology view here you can expand all
7:35 the way through from the
7:36 the edges rx through the distribution
7:38 switch into each access switch and see
7:40 all devices beyond including any access
7:42 points
7:43 just like in the listview in the
7:44 topology view you can actually click
7:45 through to the switches so let's have a
7:46 look at the distribution switch
7:48 if we look at the parts you can see that
7:50 each of the
7:52 configuration group members are color
7:53 coded across the virtual chassis
7:55 so that you can easily identify a pair
7:57 you can also see that the dedicated
7:58 virtual chassis parts are labeled with
8:00 the primary and secondary members
8:01 if you also check each of the access
8:03 switches you'll see that the uplinks are
8:04 clearly labeled and similarly color
8:06 coded where they are packed together
8:09 earlier in this video we configured a
8:11 dynamic port configuration
8:12 if we look at access switch 86
8:14 specifically i have a wi-fi access point
8:16 here
8:18 you can see that this part is actually
8:19 configured as the no access port
8:21 so without the dynamic profile this
8:23 isn't going anywhere now as i've just
8:25 reconnected this access point what we'll
8:26 actually see is the dynamic part profile
8:28 in action
8:29 you can see from the timeline that when
8:31 i disconnected the access point the port
8:32 profile is set to the no access default
8:34 however when i reconnected the access
8:36 point the profile then changes to wi-fi
8:38 ap
8:38 and it inherits the relevant
8:39 configuration
8:45 i hope this video has been helpful in
8:46 showing you how to build a medium campus
8:48 using missed wide assurance
8:49 for a deeper dive into each of this
8:51 features please do check back over the
8:52 wide assurance series playlist
8:54 thank you very much for listening