Solutions & Technologies
CUSTOMER SUCCESS
Seagate to Leverage Juniper Networks' AI‑Native Enterprise Solutions
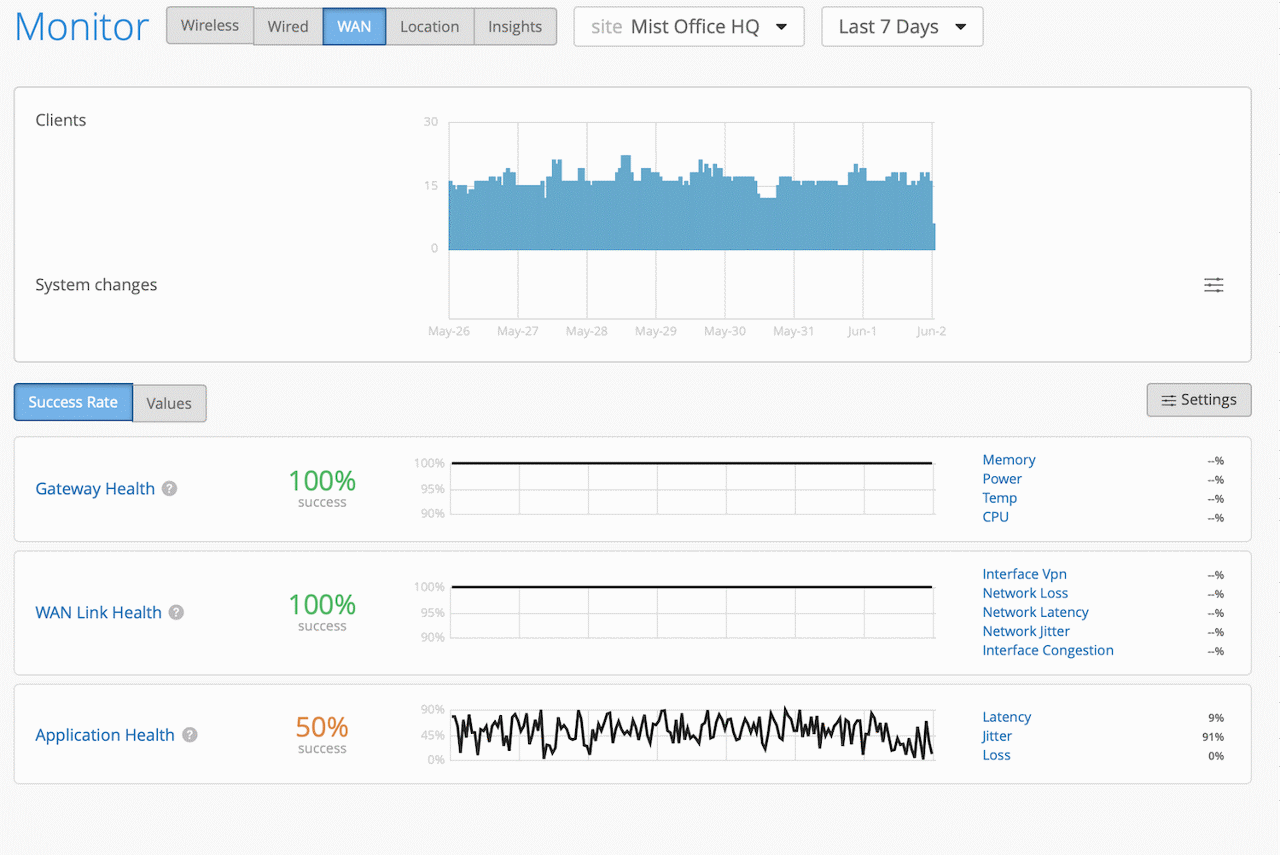
Seagate Technology® has selected Juniper’s full stack AI-native enterprise portfolio to support its evolving business needs. The Juniper solution, driven by Marvis AI and the cloud, offers Seagate proactive automation and unique client-to-cloud insight, as well as optimized performance and cost savings in key areas of their IT infrastructure.
Seagate, a world leader in mass-data storage infrastructure solutions, has multiple sites in 18 countries that share a vast amount of data. As a way of decreasing network costs and optimizing the performance of key applications between these locations, Seagate is moving from a traditional MPLS network to Juniper’s AI-native SD-WAN solution. Juniper’s unique tunnel-free SD-WAN architecture can help reduce Seagate’s telco and hosting costs, which is ideal for high bandwidth activities like data transfers.

Resource center
Analyst Reports
Videos
Infographics
White Papers
Additional Resources
Related Solutions
AI-native SD-WAN FAQs
What is AI-native SD-WAN?
Juniper AI-native SD-WAN is a tunnel-free, application-aware, and Zero Trust secure solution for reliable and secure WAN connectivity.
What products comprise the Juniper AI-native SD-WAN solution?
The Juniper Session Smart Router, Marvis AI, and Juniper WAN Assurance make up the Juniper AI-native SD-WAN solution.
What are the benefits of Juniper’s AI-native SD-WAN?
Juniper's AI-native SD-WAN delivers a multitude of benefits for modern enterprises. By consolidating essential networking components—secure SD-WAN, Wi-Fi, PoE+, switching, and optional 5G—into a single "Branch-in-a-Box" solution, it drastically reduces operational complexity and streamlines deployments. The solution is driven by Marvis AI, which automates routine tasks, proactively resolves issues before they impact users, and provides deep, actionable insights across the entire network. This approach leads to faster time to value, enhanced IT productivity, and a more reliable user experience. Additionally, the platform is built with a focus on enhanced security, including post-quantum security and seamless integration with Zero Trust and SASE architectures, ensuring that the network is protected from edge to cloud. The compact and energy-efficient design also helps reduce the total cost of ownership and promotes a more sustainable infrastructure.
What are the benefits of tunnel-free SD-WAN?
Tunnel-free SD-WAN offers many benefits, including:
- User experience guarantees, along with application performance assurances: By eliminating tunnel-based overhead, tunnel-free SD-WAN improves application performance, reduces latency, and maximizes the use of available bandwidth, enabling improved application performance and costs savings while WAN Assurance further enables better user experiences.
- Huge scale improvements: This approach also simplifies the network architecture, making it easier to manage and scale, as it removes the operational complexity of managing and orchestrating a mesh of tunnels.
- Inherent Zero Trust security: Tunnel-free SD-WAN can enhance security by applying a Zero Trust model that encrypts and authenticates each individual session, rather than relying on a complex and potentially less secure tunnel infrastructure. This provides a more secure, streamlined, and high-performing network fabric.
How does tunnel-free SD-WAN secure traffic?
Tunnel-free SD-WAN secures traffic by applying a Zero Trust security model and per-session encryption instead of relying on a traditional tunnel infrastructure.
Deny-by-default and session-awareness
Unlike traditional SD-WANs that often operate with an "allow-by-default" approach within a secure tunnel, tunnel-free SD-WAN uses a deny-by-default policy. This means that a session is not trusted or allowed to communicate until it has been explicitly authorized. The system authenticates and verifies each individual session and its intent before permitting any traffic.
This security is applied on a hop-by-hop basis, with each router in the fabric validating the session's legitimacy. This process creates a secure fabric that builds trust from the ground up, rather than assuming trust within a large, pre-established tunnel. This granular approach makes it difficult for a threat to move laterally across the network, as unauthorized sessions are dropped immediately.
Integrated security functions
Tunnel-free SD-WAN weaves security directly into its fabric, rather than relying on a separate security appliance. It combines a service-centric control plane with a session-aware data plane to apply security policies, quality of service (QoS) parameters, and access controls on a per-service or per-network basis. This integrated approach can include features like:
- Zero Trust security boundaries to compartmentalize different areas of the network
- Next-generation firewall (NGFW) capabilities
- Proactive analytics to detect threats in real time
This security model is designed to be highly scalable and efficient, as it avoids the operational complexity and bandwidth overhead associated with managing a large number of tunnels.
What are the limitations of tunneling protocols like IPsec?
Performance overhead: The process of encapsulating and encrypting every packet adds a significant amount of data to each packet, which reduces network efficiency and can increase latency. This is particularly noticeable in high-speed or low-latency environments. (We refer to this wasted overhead as badput.)
Configuration complexity: IPsec is not a single protocol but a suite of protocols, making it complex to configure. This can lead to a high potential for error, creating security gaps or network outages. Different vendors may also have slightly different implementations, leading to interoperability issues.
Scalability challenges: In large, distributed networks, managing a full mesh of IPsec tunnels can become an immense operational burden. Each new location requires the creation and management of new tunnels, which doesn't scale well and becomes a bottleneck for expansion.
Zero Trust limitations: Traditional IPsec tunnels create a broad "trusted" network. Once traffic is inside the tunnel, it often has wide access to other network resources, which can be a security risk. A tunnel provides a sense of security between two points but does little to protect against lateral movement of threats once inside the network.
What are the scaling differences between tunneled SD-WANs and session-intelligent, tunnel-free SD-WANs?
Tunneled SD-WANs, which typically rely on protocols like IPsec, face significant scaling challenges. To connect a growing number of sites, a full-mesh network requires a massive number of tunnels. The formula for a full mesh is n(n−1)/2 tunnels, where 'n' is the number of sites. As the number of locations increases, the number of tunnels and the associated management overhead grow exponentially. Each tunnel requires careful configuration and maintenance, and misconfigurations can lead to security vulnerabilities or connectivity issues. This complexity creates a bottleneck for expansion and can make troubleshooting a "needle in a haystack" problem. Furthermore, the overhead from encapsulation and encryption in each tunnel reduces bandwidth efficiency, a problem that is compounded as the number of tunnels and traffic volumes increase.
Session-intelligent, tunnel-free SD-WANs, in contrast, scale far more gracefully. They do not rely on tunnels and instead use a deny-by-default, service-centric architecture. This means the network fabric is built on a simple, scalable, and secure routing foundation. Rather than managing thousands of tunnels, the system manages sessions that are authorized and encrypted individually. This eliminates the configuration complexity and exponential tunnel growth. As new sites are added, the fabric automatically extends to them without the need for manual tunnel setup. This approach also maximizes bandwidth efficiency by removing the overhead associated with tunneling protocols. The result is a highly scalable, agile, and simpler network that can easily accommodate rapid business expansion and the dynamic demands of a cloud-focused enterprise.
What are the main security features in Juniper’s SD-WAN solution?
Juniper's SD-WAN solution is designed with security as a core component of the network fabric, not as an afterthought. It moves beyond traditional, perimeter-based security to a more integrated, proactive, and future-ready approach.
Here are the main security features:
- Zero Trust architecture: The solution is built on a deny-by-default model. This means traffic is not trusted until it's explicitly verified and authorized, both at the initial point of access and at every hop across the network. This approach significantly reduces the attack surface and prevents the lateral movement of threats
- Per-session security and encryption: Instead of relying on a large, "trusted" tunnel, Juniper's SD-WAN secures each individual session. This granular control allows for the application of security policies and encryption on a per-service or per-application basis. This provides more control and makes it harder for a threat to compromise the entire network
- Integrated firewall and threat prevention: The SD-WAN platform includes built-in security functions, such as a fully-fledged next-generation firewall (NGFW), as well as features for intrusion detection and prevention (IDP). This eliminates the need for a separate security appliance at each branch and centralizes management
- Secure boot and hardware-assisted security: For security-sensitive environments, the solution features hardware-assisted secure boot, ensuring the integrity of the device and its software from the moment it powers on
- SASE and Zero Trust integration: The solution is designed to work seamlessly with Secure Access Service Edge (SASE) and Zero Trust architectures. This allows enterprises to combine networking and security into a single, cloud-delivered platform for consistent policy enforcement across the entire network
What are the deployment options for Juniper’s AI-native SD-WAN?
Juniper’s AI-native SD-WAN is powered by the Session Smart Router, which is software-based and deployable on Juniper SSR Series Routers, white-box customer premises equipment, data center network servers, and the cloud. Session Smart Routers can be managed on premises or in the cloud by the Session Smart Conductor or via the Juniper Mist cloud.
Who should use the Juniper AI-native SD-WAN?
Small- and medium-sized businesses, enterprises, telecommunications providers, and managed service providers looking to modernize their network and improve network user experiences should all consider Juniper’s AI-native SD-WAN.
What are the use cases for Juniper’s AI-native SD-WAN?
Juniper’s AI-native SD-WAN supports the following use cases:
- Simplified branch deployments (Branch-in-a-Box)
- Operational efficiency and proactive troubleshooting
- Secure and compliant networking
- Optimized application and user experience
- Cloud connectivity and multicloud integration
Where can I get help with the Juniper’s AI-native SD-WAN?
For information regarding AI-native SD-WAN deployment services, read the AI-native SD-WAN Deployment Services datasheet. For help with the Session Smart Router, view our Session Smart Router documentation, take a training course, or join our SD-WAN Community.