SD-WAN Explained
A Brief History of WANs
The concept and implementation of a WAN (wide area network) first came about as a means of facilitating remote terminal access to mainframes and minicomputers. From arguably the first clouds that used X.25 in the 1970s and 80s to Frame Relay in the early 90s, it wasn’t until IPsec VPNs and MPLS VPNs in the late 90s that WANs became more predominant.
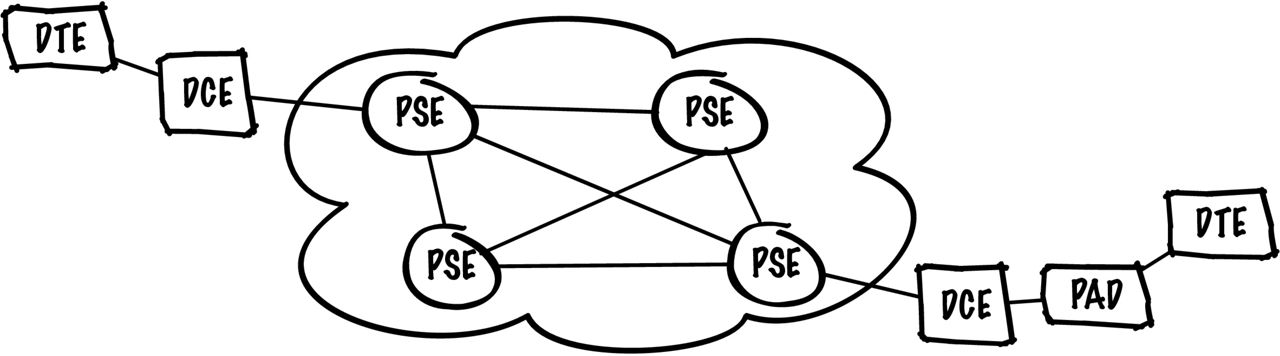
X.25 Network
Just as the rise of the Internet has spawned many innovations at scale, there has been a constant desire to reduce the cost per bit of bandwidth, especially across expensive WANs. As broadband connections became more ubiquitous, organizations began to use these connections as cheaper paths for multiple types of traffic across different scenarios.
In the early 2010s, SDN (software-defined networking) began to be recognized as an approach that could reignite innovation in data networking. Its goal was to abstract networks further for a range of functional, operational, and performance gains. Early goals sought to disaggregate networking hardware and software, standardize the control plane, and deliver more openness. SDN also sought to accelerate innovation cycles. Just as compute and storage had gone through major evolutions and shed levels of complexity, SDN began to rewrite the “how” not just the “what” of networking.
It’s from the SDN school of thought that SD-WAN (software-defined wide area network) was born. SD-WAN technology is not one specific WAN architecture but rather a concept and abstraction that seeks to address many of the constraints and shortcomings experienced with traditional WANs.
WAN Challenges
Even with dynamic routing protocols, rarely are WAN paths optimized for anything more than the most basic reachability. CSPs (communications service providers) may make the most extensive use of routing metrics such as latency, jitter, and packet loss, along with policy-based techniques, to apply their business practices and optimize costs for deploying failover links and other customer experience enhancements across the WAN. For many organizations, however, such tasks are complex, time-intensive, and cost-prohibitive.
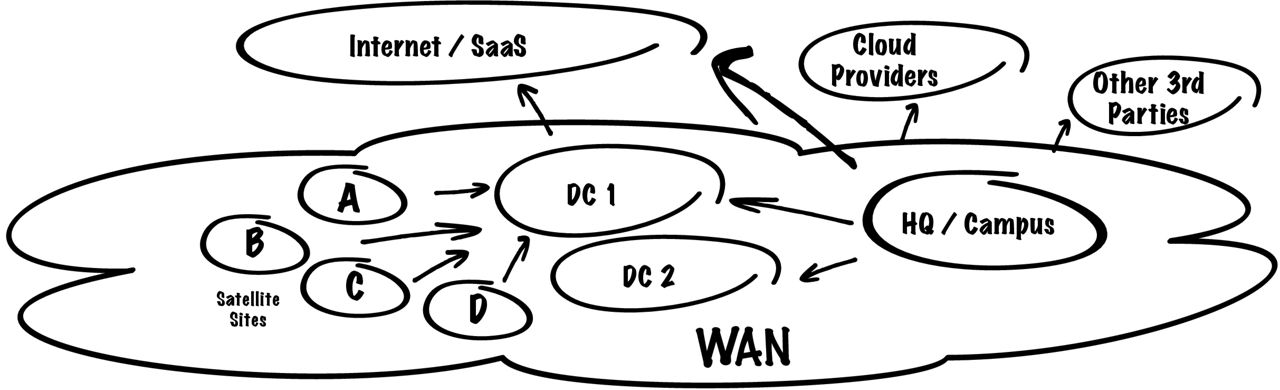
Complex Pathing for Critical Footprints
On the other hand, enterprises whose WANs rarely generate revenue are often beset by productivity-impacting issues that result in a loss of user confidence. This loss can be due to suboptimal WAN performance, outages, or maintenance tasks that affect business-critical workflows and communication.
Although dynamically routed, traditional WAN orchestration and operations are burdened by a lack of situational awareness related to individual user sessions and the extent of the footprints they serve. Modern multimedia applications such as voice, videoconferencing, gaming, and a host of other latency-sensitive apps require constant peak performance. They do not suffer congestion or packet loss well.
So, what are some of the problems or challenges an SD-WAN aims to solve?
- Expensive WAN connectivity
- Operational complexity
- Limited controllability and coarse metrics
- Service brittleness
- Lack of application and session awareness
- Suboptimal performance, congestion, and complex queueing
- Limited scalability and elasticity
- No default defensive security posture
- Applying or embedding business policies
The SD-WAN Promise
As mentioned, SD-WAN is a concept and an abstraction layer. It’s a networking approach that has varying architectures, implementations, and goals but is focused on improving all facets of WAN service delivery. A natural offshoot of SDN, SD-WAN makes a WAN more malleable, programmable, and intelligent. This approach facilitates new functionality, improved service delivery, and reduced costs. Additionally, SD-WAN plays a role in evolving models of infrastructure management, monitoring, and security.
SD-WAN Meaning: What Exactly Is Software-Defined?
Whether to simplify orchestration, add more programmability to a WAN, or deliver a new overlay virtual network, SD-WAN means different things to different people (hence the somewhat ambiguous nature of the term). What does software-defined mean relative to the WAN?
Rather than let traditional network operating systems and static configurations define the totality and operation of a WAN, SD-WAN presents a new interface or platform that is influencing or providing WAN functionality and features. Everything from orchestration, operations, and low-level packet control can be driven by this new (and often centralized) software platform.
SD-WAN is not just a reinterpretation of an NMS (network management system). It represents a paradigm shift in reshaping and controlling low-level and high-level WAN functions. By embracing the approach and benefits of SDN (commonly seen in modern data centers), WAN services can evolve and adapt more quickly to an organization’s changing needs and requirements.
SD-WAN Solutions: Defining and Redefining the WAN
Traditional WAN
Although networks with dynamic routing protocols are themselves a type of distributed system, SD-WAN implies the use of intelligent logic to provide a new service overlay or interfaces to drive, accelerate, and optimize the WAN in real time. Enhanced logic, additional automation, and new features are orchestrated and controlled from this platform. Some SD-WANs can also directly engage with an existing underlay (via traditional routing protocols) and provide a whole new virtual overlay plane for packet control, steering, and forwarding.
SD-WAN comes with varied architectures. Often SD-WAN entails a centralized physical, virtual, or cloud-based controller. Some solutions augment the underlay WAN with new physical or virtual nodes. Most organizations take advantage of market-based SD-WAN solutions, while a few build their own solution platform subject to the right internal expertise and willingness.

SD-WAN (Software Defined WAN)
With the new system interfaces and overlays, SD-WAN can redefine and transform traditional WAN service delivery and operations. Where reachability and reliability were the conventional building blocks of existing underlays, SD-WAN addresses the need for a more aware, intelligent, and resilient network.
SD-WAN: A New Approach
Goals of an SD-WAN
Although organizations may have differing goals for deploying an SD-WAN, they generally seek a blend of common business and technical requirements:
- Simplified operations with greater network resilience
- More intelligent pathing, orchestration, and agility
- The ability to embed business logic and policy deep into the network
- Reduced transport costs and optimized resource utilization
- Better observability and application analytics
- Application acceleration (increasingly for SaaS applications sensitive to latency, loss, and jitter)
- Increased security with fine-grained policy control
- Improved user experience and better quality of service
- Programmability, wider automation, and more modern APIs
SD-WAN Benefits and Drivers
As technology morphs and changes, so too do network traffic patterns. Organizations continually seek to better manage network complexity, all while controlling costs and providing the best services they can to their customers and employees. As cloud-based services usher in greater demands on WAN connectivity, the services being accessed may result in flows along trusted or untrusted paths. Depending on the transport used, these paths may make use of shared rather than dedicated links and may not offer multiple classes of service.
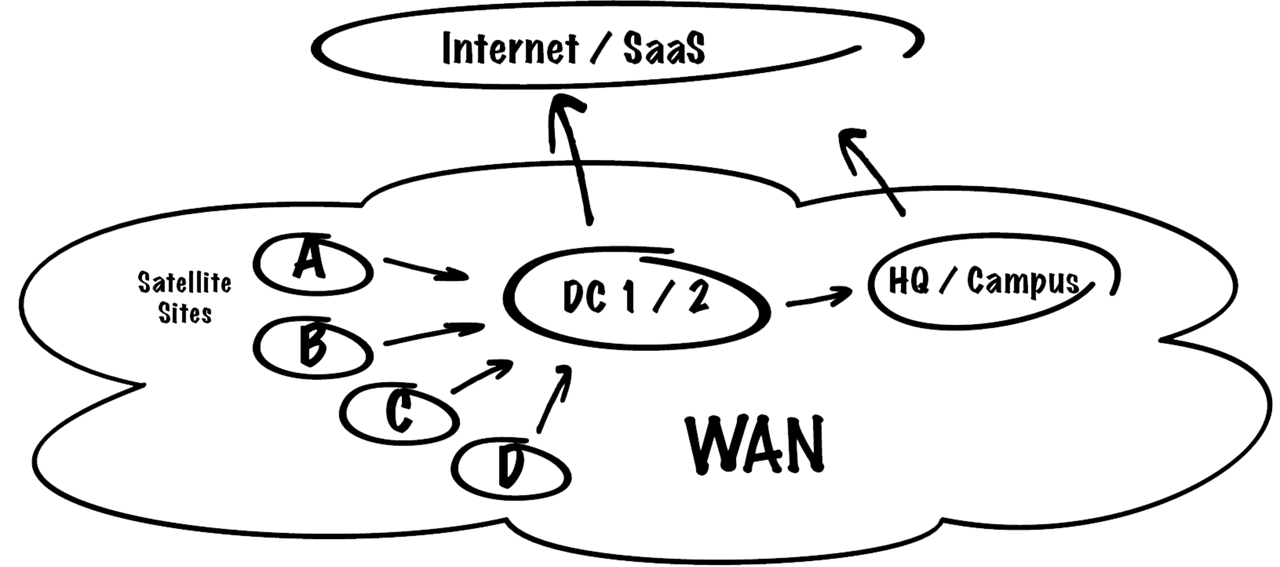
Traditional Centralized Internet Access
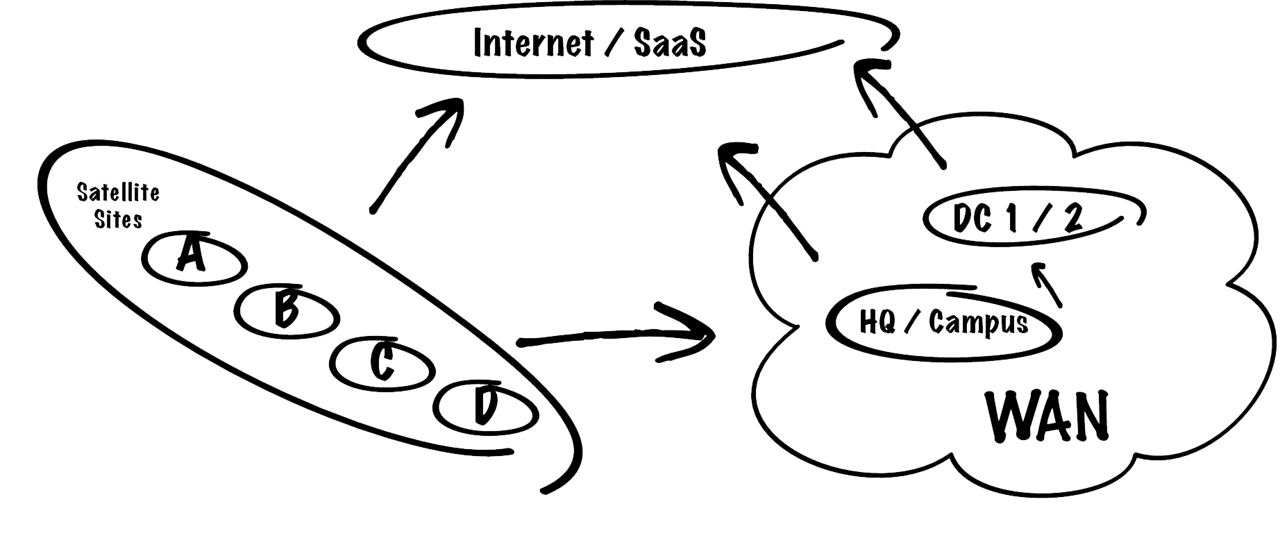
Leveraging Direct Internet Access
To simplify, unify, and secure multiple access types, be they branch, campus, data center, or otherwise, SD-WAN solutions promise greater elasticity, agility, and security delivered in a range of form factors and business models. When evaluating SD-WAN solutions, it’s imperative that organizations are clear about their motivations, requirements, and desired outcomes, not just for Day 0 (design), but all the way through Day 1 (deploy), Day 2 (operate), and beyond.
Who Does SD-WAN Benefit?
SD-WAN benefits large-scale network operators, smaller players, and everyone in between. SD-WAN is not just about enhancing orchestration, operations, and security, but also about enhancing service delivery and improving the quality of user experience. Network operators, a company’s bottom line, and WAN users, whether human or machine agents, all benefit.
For NSPs (network service providers), SD-WAN implementations enable them to offer more robust and enhanced WAN services. SD-WAN is evolving toward becoming a form of IaaS (infrastructure as a service), which can be applied internally or as an MNS (managed network service) at the network edge. As SD-WAN-powered managed WAN services grow in popularity among enterprises, large campuses, and retailers, SD-WAN service providers will continue to innovate their offerings. Many already offer features like ZTP (Zero Touch Provisioning) and ZTC (Zero Touch Configuration) to reduce friction, scale operations, and improve time to delivery and time to value.
Across all organizations, network and security teams that embrace SD-WAN have the capabilities to improve services, decrease response times, and most of all, remove everyday toil. The less time IT teams spend on keeping the lights on, the more time they can spend on projects that help move their business forward. Any business workflow, network flow, or workload that relies upon a WAN has the potential to benefit from SD-WAN features and functionality, resulting in a higher-performing, more resilient, and secure organization.
SD-WAN Architecture
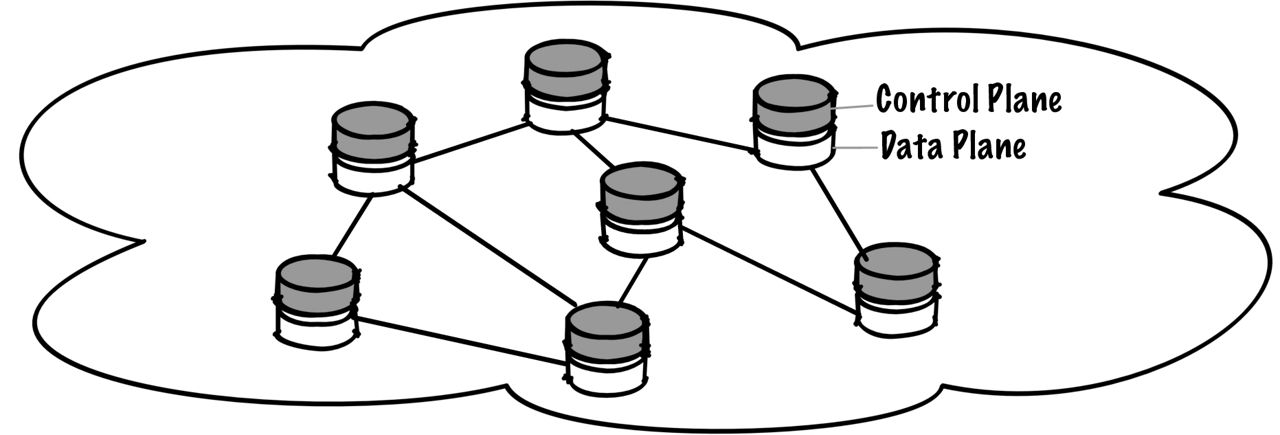
One of the original goals of SD-WAN was to separate the data and control plane to facilitate higher-order logic and intelligence. Yet there still is no single unified SD-WAN network architecture. There are many approaches and variants, and some people might argue that automated orchestration and operations can also constitute an SD-WAN.
There are, however, common building blocks and boundaries that constitute SD-WAN as a conceptual delivery model. It can be thought of as a platform that may engage with, augment, or displace elements of a WAN and its operation, by either integrating with or replacing network functions in the data and control planes.
SD-WAN designs and solutions also typically play a major role in network provisioning, orchestration, management, and monitoring, while some deliver far more dynamic and granular capabilities for performance, policy, and security requirements.
Even with differing business models and use cases, SD-WAN commonly includes a centralized controller and either a full or partial mesh (versus a traditional hub-and-spoke topology). Although an SD-WAN may leverage an underlying traditional or hybrid WAN to build its new transport overlay, it’s an OTT (over-the-top) model that enables the most rapid deployments and lifecycle management, thus avoiding costly rip and replace upgrades.
Tunnel-Based or Tunnel-Free Designs
Tunnels create packet overheads and increase fragmentation. Additional data and increased processing overheads negatively affect throughput and performance. Tunnel-based approaches also complicate and hinder scaling while contributing to slower session failover across backup paths. Additionally, even when tunnelled, there’s an inability to apply security policies mid-flight until subsequent decapsulation allows for inspection, identification, and profiling from behind the tunnel endpoint.

Tunnel-Based Configuration and Encapsulation

Tunnel-Free Session Based Steerability
Newer tunnel-free approaches reduce SD-WAN packet overheads and maintain optimal throughput without using costly encapsulation. This approach also supports rapid scaling and, while not infinitely scale-free, requires a lot fewer resources and configuration to deliver a growing any-to-any topology. Tunnel-free also facilitates better situational and session awareness, leading to the ability to steer flows and apply security policies earlier.
SD-WAN Deployment
As mentioned, SD-WAN may come in many forms (and form factors), but the most popular involve the least amount of real-world friction. Some scenarios use an on-premises appliance or whitebox, but most SD-WAN architectures and solutions offer virtual machines and virtualized network functions that can be wholly software provisioned on existing servers and routers.
Just as a traditional WAN provides connectivity and transport between sites, assets, and services, an SD-WAN can also extend an intelligent edge or mesh to anywhere there are managed entities or agents (even when using unmanaged underlays):
- Branch and remote office to corporate
- Distributed campus
- Data center to data center
- Remote access
- Corporate to public or private cloud
- CSP or ISP core/edge
As SD-WAN is not an explicit protocol or technology, many implementations of SD-WAN overlay make use of disparate underlying wired and wireless transports or technologies, including but not limited to SD-WAN over MPLS VPNs, DSL, and 5G/LTE (or other wireless backhauls).
SD-WAN vs. MPLS
SD-WAN doesn’t directly replace MPLS VPNs but can offer an alternative when combined with other transports. SD-WAN integrates with a whole host of WAN technologies across disparate architectures. Different flavors of SD-WAN will easily leverage existing MPLS services and build their own new topology or overlay, some of which are tunnel-less. By dramatically decreasing data encapsulation overheads, these tunnel-free SD-WAN solutions immediately address cost optimizations on a wide variety of links while maintaining security and associated confidentiality.
In certain scenarios, SD-WAN implementations can diminish the need for MPLS VPNs by using more cost-efficient connectivity options while maintaining many of the characteristics of more expensive transport options.
The Keys to SD-WAN
All About User Experience
It’s often assumed that an organization knows exactly who and what is using its WAN. But it's not until the flows and sessions are analyzed can an organization truly understand who the actual users are and what their use cases really consist of.
Over time network usage oscillates and alternates between machine-based agents and user-initiated traffic. The WAN itself is a finite resource, and as traffic patterns morph, some sessions and flows encounter congestion. These sessions can and should be immediately prioritized or steered via alternate paths, but this isn’t always the case.
Congested paths are unable to meet the demands of real-time communications, and this has always been a challenge for WAN service delivery. Previous generations of SD-WAN solutions have provided mostly static implementations that use QoS (quality of service) markings and queueing strategies, but rarely can they dynamically influence and steer individual sessions to improve a user’s flagging experience in real time. Some SD-WAN solutions can even provide for symmetric session pathing for optimized performance and policy adherence.
Session awareness is a crucial component of modern SD-WAN solutions. It offers the best fidelity view of a network from the user’s perspective. Sessions are temporal and involve specific application flows whose quality can differ greatly (due to factors such as capacity, delay, congestion, and intermittent outages). Session awareness goes further than standard application identification and can be used by an intelligent fabric to direct individual sessions for each and every user or agent on a session-by-session basis. By taking a more holistic and unified view, tied with a fine-grained capability to route traffic flows, some SD-WAN solutions can automatically elevate, demote, or selectively steer these sessions based upon criteria such as service-level objectives. Individual sessions have become the ultimate currency for network operators to deliver superior user experiences.
WAN Assurance
Assurance is a means of providing confidence. The WAN is critical, not just for connecting sites but for accessing services and resources and expediting workflows. Confidence brings peace of mind. Whether provisioning new locations, scaling capacity, or helping ensure that security and operational teams have the right tooling and support, it’s crucial for network operators to have the right capabilities. Operations is not just about performing well, but more importantly, failing well and minimizing harm. Outages and congestion may occur, but with an intelligent overlay, less time is spent worrying about MTBF (mean time between failures) and MTTR (mean time to repair).
Where historically, IT teams were limited by the metrics or tradeoffs of traditional routing protocols, there is now an option to virtualize the WAN itself while adding new layers of intelligence and better feature velocity. SD-WAN promises more fine-grained control of packets and their flows and opens up endless possibilities on how to implement everything from better security policies to improved cost controls, all the while improving user experience.
Connected Security and SASE
Security is about risk. In a world of borderless and accelerating digital threats, organizations strive to protect their assets, services, and staff. Increasingly digital security impacts safety. The risks related to intentional attacks have also begun to impact other elements of operations. The more digital connectivity and control there is, the wider the digital attack surface that requires protection.
Security architectures have long sought to limit and partition failure domains against the propagation of failures, but there is a real struggle on how to do so without adversely impacting the smooth running of workflows and processes. SASE (Secure Access Service Edge) offers a combination of security functions delivered at trusted boundaries that limit the traditional overheads associated with remote-access solutions.
When SD-WAN is understood as a conceptual delivery model for services, it can then be understood as underpinning many security best practices. It’s not a matter of SD-WAN vs. SASE but the knowledge that SD-WAN delivers the foundational building blocks of SASE. The network is still one of the best places for many security controls. The WAN edge creates an efficient and effective policy enforcement point, and one that also provides the means for better observing and controlling zone boundaries and related security requirements. With ZTNA (Zero Trust Network Access), the coin firmly lands on “default deny” posture being the most advantageous and robust compared to less secure “default permit.”
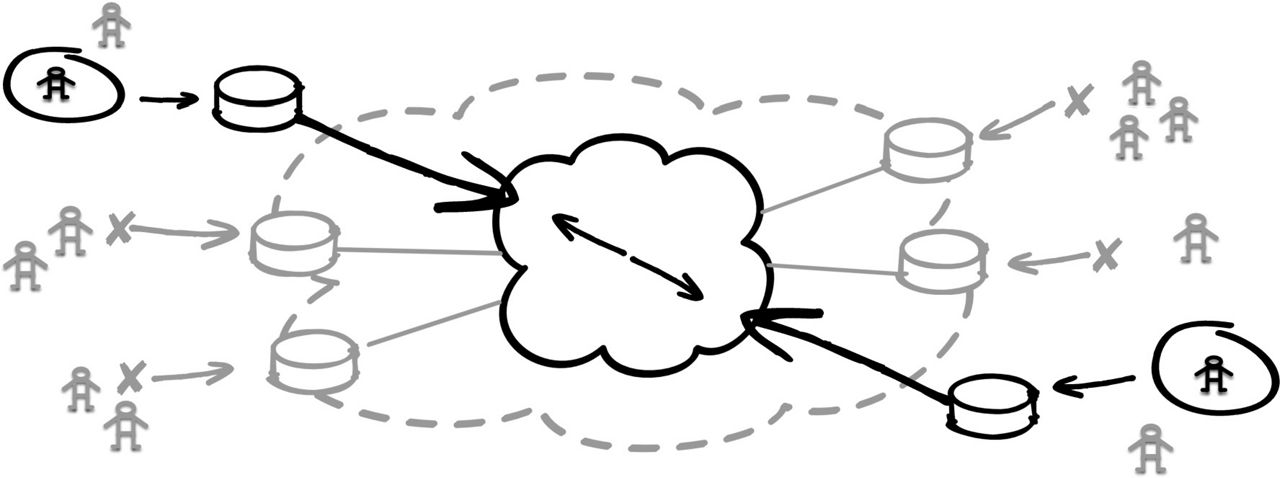
Zero Trust Network Access
(Requires Explicit Permit)
The remaining challenge is to help ensure that complexity is controlled and managed. When microsegmentation and micropermissions are bound by granular IAM (Identity Access Management), assigning permissions, access, and roles manually becomes too tedious. Increasingly, organizations are turning to automation and software-based solutions to handle IAM.
SD-WAN is poised to help deliver on the promise of increased security, elevated confidence, and greater peace of mind by reinforcing the strongest policy enforcement points possible, the network.
Operator Experience
In the quest to reduce TCO (total cost of ownership), it’s often OpEx (operational expenditure) that outstrips CapEx (capital expenditure) over a given timeframe or lifecycle. Complex systems imply operational complexity, but this isn’t always so. Just as abstractions enable network operators to do more with less, so too does SD-WAN deliver on simplified management and operations that can empower IT teams to exceed expectations.
Teams that embrace tooling and approaches that intelligently remove or reduce toil enjoy greater satisfaction, resulting in lower employee churn and greater productivity (2020 SoNAR–State of Network Automation Report).
At the end of the day, it's the operations teams that dictate the technical health of an organization, and thus IT can have an outsized impact on an organization’s success or failure. Widespread failures become visible not just to users but also customers and eventually the market at large. Although cost savings and security are key areas targeted by SD-WAN, they’re not the only SD-WAN ROI (return on investment) that can be taken advantage of.
The AIOps Advantage
AI (artificial intelligence), and one of its subsets, ML (machine learning), can deliver tremendous value throughout the networking domain. Problem areas that have well-known features and protocols (such as data networking) are ripe for the use of ML in a host of scenarios. In these well-defined problem spaces, AI bias can be easily removed to deliver on real-world outcomes, in addition to better network connectivity and security. When training ML with a mix of blended and accelerated learning (such as Transfer learning) and then augmenting AI with production data, trust can be built quickly. Accurate insights and recommended remediation actions surface and can be quickly validated.
Data networking is an area where the volume and velocity of operational data and telemetry constantly outstrip the ability of traditional methods to keep pace. Networks are graphs. AI and ML can offer rapid and actionable insights into graphs and their dependencies, including everything from identifying complex root causes to providing better interfaces to navigate and manage increasing network complexity.
AIOps (artificial intelligence for IT operations) is a practice that seeks to ease the burden on network operators by automating many repetitive and low-value tasks that create toil. Freeing up human talent for more strategic challenges is a crucial step in innovation, as is democratizing the ability to make sense of the growing networks and complexity that surrounds us.
Resource Center
Customer Case Studies
Webinar
SD-WAN FAQs
What does SD-WAN mean?
SD-WAN means a wide-area network with its fundamental functions abstracted. It’s centrally controlled by an intelligent software platform rather than being wholly distributed, decentralized, and reliant upon discrete network operating systems. This concept provides a more programmable control plane with increased observability, responsiveness, and controllability.
What does SD-WAN solve?
SD-WAN solves many of the challenges of traditional WANs, such as operational complexity, limited controllability, coarse metrics, service brittleness, and suboptimal capacity management. Additionally, greater security and more fine-grained business policies can be embedded while reducing operational costs.
How does SD-WAN work?
As an abstraction layer, SD-WAN provides simpler orchestration and optimized operations. At the architecture layer, there are different approaches, but SD-WAN usually becomes an overlay on a physical network. The control plane is centralized while additional features and functionality can be rapidly layered on. SD-WAN then allows for unified logic with centralized workflows and APIs.
Is SD-WAN a router?
SD-WAN is not a single router but can encompass and perform the role of many routers. Different approaches involve augmenting physical or logical routers, while other solutions replace existing nodes completely.
Does SD-WAN replace a router?
It depends on the solution. Some SD-WAN offerings replace routers and other nodes completely. Lower-friction approaches augment existing nodes or provide new logical gateways.
Is SD-WAN a routing protocol?
SD-WAN is a concept and abstraction layer that, once instantiated, can incorporate new routing protocols but often leverages existing ones. Commonly, SD-WAN provides an overlay to an existing underlay network and then delivers additional value across all services and operations.
What is the difference between SD-WAN and WAN?
An SD-WAN is an enhanced WAN that offers additional features over and above basic reachability and traffic engineering. A traditional WAN is composed of routers, each running a network operating system with its own control plane based upon local configuration and state information. An SD-WAN typically centralizes the control plane and shares state across all nodes.
What are the advantages of SD-WAN as compared to a traditional WAN solution?
SD-WAN offerings can improve security posture, lower operational costs, and enable more fine-grained and intelligent decision-making, especially for performance and capacity. User experience and operator experience can be significantly improved, while superior scalability and elasticity can be achieved using global and local views of WAN conditions.
How does SD-WAN improve network performance and make WANs agile?
SD-WANs use additional telemetry to increase the overall observability of a WAN. This can include individual session and flow metrics that impact user experience. With more holistic and fine-grained traffic engineering comes the ability to rapidly influence and control performance using smarter logic and intelligent policy. Additionally, orchestration and lifecycle management are simplified due to centralized platform logic, which increasingly incorporates artificial intelligence (AI).
What is SD-WAN dynamic routing?
Although most WANs rely on dynamic routing, the metrics used can be considered coarse and concerned only with reachability. SD-WANs can interact with the underlay routing (if so desired) but build overlays using enhanced dynamic routing that takes advantage of intelligent insights into the over-the-top (OTT) services provided to end-users.
Is SD-WAN better than MPLS?
SD-WAN is not a specific protocol or standardized architecture but can leverage and enhance existing services provided by an MPLS footprint. SD-WAN also allows for a wider selection of lower-cost transport technologies and media (not just MPLS-related) depending on an organization’s business and technical requirements
Does SD-WAN replace VPN?
Different SD-WAN offerings form their own type of site-to-site virtual private network (VPN) and can integrate with or sit behind remote-access VPNs. Some SD-WAN offerings solve security challenges in different ways while improving the integrity, availability, and performance of the WAN.
Does SD-WAN replace DMVPN?
Depending upon requirements, SD-WAN may replace some dynamic multipoint VPN (DMVPN) footprints by providing a secure and scalable transport that requires little to no orchestration (such as those that use zero-touch provisioning). Usage is highly dependent on the SD-WAN offering and use case, but one of the goals of SD-WAN is to provide similar functionality to DMVPNs.
Does SD-WAN use IPsec?
Most SD-WAN solutions and vendors use standards-based protocols, while some have created their own proprietary protocols. An SD-WAN may enhance or replace an existing WAN and VPN, which will dictate whether an SD-WAN offering must integrate with or use IPsec.
What are some of the weaknesses of SD-WAN?
Moving from a distributed to a centralized control plane may be seen by some as a weakness, though there is often already some form of centralized operations, orchestration, and governance in WAN management. SD-WANs seek to reduce operational errors and common-mode failures while providing a more robust overlay, even when traditional underlays and routing are still in play.
Is SD-WAN a private network?
SD-WAN can be a wholly private network or multitenanted, depending on the specific use case, service offering, and network intent. SD-WAN may offer different levels of privacy and can be dedicated to a single organization; it can also be part of a managed service offering or customer-administered as part of a cloud offering.
Is SD-WAN a VPN?
SD-WAN could be thought of as a type of VPN, though the concept of SD-WAN is more about the abstraction, programmability, and flexibility of the WAN than it is about security. An SD-WAN can share similar goals and provide similar services to a VPN, but not all SD-WANs are VPNs.
Is SD-WAN secure?
SD-WANs adhere to fundamental security tenets such as confidentiality, integrity, and availability. They’re generally built to be secure by default and provide protection from intentional harm while preventing unintentional failures. As always, and irrespective of technology, protocol, or configuration, operational security is an ongoing process that requires management, oversight, and maintenance.
How does SD-WAN improve security?
SD-WAN can more readily implement and enforce strategies such as defense-In-depth and zero trust access control, in part due to its centralized command and control structure. Fine-grained policy enforcement and orchestration facilitate consistent “least privilege” controls and ensure that deny-by-default is mandated across the board rather than the more permissive permit-by-default of traditional WANs. By leveraging secure protocols and increased telemetry for better visibility into the network, SD-WAN can observe, identify, control, and mitigate threats faster than individual point solutions located at boundary points. Security can be embedded throughout the whole WAN.
Do you need a firewall with SD-WAN?
Depending on your security posture and existing policy enforcement points, you may not need additional security layers when deploying an SD-WAN. Modern SD-WAN offerings include a range of network- and application-level security capabilities. Many of these features obviate the need for certain functions of firewalls. Enhancing your security posture on the WAN at both network and application layers can be hugely beneficial to an organization’s security posture, particularly when adopting zero trust strategies.
Who buys SD-WAN?
SD-WAN is a concept and abstraction that organizations can choose to build from the ground up, buy from a trusted vendor, or consume as a managed service delivered by a cloud or service provider. Those without the necessary development expertise, budget, time, and resources to build their own will buy and implement vendor SD-WAN offerings or use a managed service. This option allows small, medium-sized, and large organizations to focus on their core competencies while benefitting from the product development, support, and maintenance offered by vendors, cloud, and service providers.
How can I improve my SD-WAN?
There are many approaches to developing and improving SD-WAN solutions. If you don’t use an AI-driven SD-WAN, traditional operational tasks usually remain cumbersome. These includes constant monitoring, performance management, refinement of traffic and security policies, and ongoing lifecycle management. There are many areas where improvement may be warranted but reducing overall operational toil using AI and automation is key to freeing up human time to focus on higher-impact initiatives.
How much does SD-WAN cost?
There’s no specific price for an SD-WAN as there are multiple approaches and vendor offerings. SD-WAN should, however, lower circuit costs and operational overhead. It should dramatically reduce the time to deploy new sites and topologies while improving user and operator experiences.
What is ZTP in SD-WAN?
ZTP, or zero-touch provisioning, means there is no requirement to bootstrap and locally configure SD-WAN nodes. These tasks are taken care of centrally and are automated. Typically, only non-default templates or profiles must be selected at a central location, while all other provisioning is automated.
What is the primary distinction between the SD-WAN use case and the hybrid WAN use case?
A hybrid WAN makes use of multiple transport and connection types. Hybrid WAN leverages different layers and technologies such as MPLS, leased lines, VPLS Ethernet, and broadband direct Internet access (DIA). SD-WAN is an overlay technology that typically runs on top of these physical networks. SD-WAN is more focused on overlay reachability, traffic engineering, and value-added services riding on top the physical WAN.
What are the components of SD-WAN?
SD-WAN normally comprises a highly available central controller and orchestration function that programs and manages edge nodes. These edge nodes can also provide a range of services to the SD-WAN as dictated by the SD-WAN offering. The controller typically provides all orchestration, management, and reporting functions while using the context gained from the edge nodes to make better global routing, policy, security, and service enhancement decisions.
Does SASE need SD-WAN?
Secure access service edge (SASE) is an evolution and complement to SD-WAN that delivers comprehensive security functions, including identity-related services, throughout the WAN. SASE relies on a cloud-based set of security functions, referred to as the secure service edge (SSE). SASE, then, can be thought of as SD-WAN plus SSE. SSE is typically cloud-based and can be supplied by a specific vendor, whereas SD-WAN can be physical, logical, and/or cloud-based while integrating laterally with other providers.
Should I use a managed service provider for SD-WAN?
The answer depends on multiple criteria. These include how complex your WAN is, team resources and competencies, and budget.
Who provides SD-WAN services?
SD-WAN services may be provided by the vendor that sells the solution, by cloud services companies, or by managed service providers specializing in SD-WAN. Professional services such as design, deployment, and operation are also available from most vendors to cover your day-0, day-1, and ongoing needs.
What is DIY SD-WAN?
Do it yourself (DIY) SD-WAN means building all facets of an SD-WAN solution yourself. The project involves writing all the software for both the controller and SD-WAN edge nodes and taking responsibility for all aspects of the software and system lifecycle management. Building a DIY SD-WAN is a complex undertaking that’s embraced mostly by hyperscale cloud providers with vast IT resources and budget available to them.
Who Does SD-WAN Benefit?
SD-WAN benefits large-scale network operators, smaller players, and everyone in between. SD-WAN is not just about enhancing orchestration, operations, and security, but also about enhancing service delivery and improving the quality of user experience.
























