A Serious Discussion About Data Center Management in the Cloud Era

Your data center must evolve for the cloud era. Here’s how.
Rapid data center growth is expected to continue into the future, which means network operators and architects will need to do more with less. In this first episode of Experience-First Data Center Networking Series, Juniper’s Majid Ansari and Jeff Doyle dish on the future of data center management in the cloud era.
You’ll learn
Solutions for modern data center challenges
An intent-based approach for EVPN-VXLAN operations and fabric management essentials
How Juniper Apstra can help you reimagine data center operations with continuous automation and assurance
Who is this for?
Host

Guest speakers

Transcript
0:00 [Music] good morning folks and thanks for
0:06 joining us today uh this is the first lighting talk uh this is the first lightning talk in our experience first
0:12 data center networking series today we'll talk about modern data centers architecture uh with abstract my
0:19 name is majid ansari and i'm an architect for cloud vertical with us we have jeff doyle we all know
0:25 jeff and thank him for educating us through the years with his books trainings videos and blogs uh thanks for
0:32 joining us uh jeff um so today uh we're gonna talk about data
0:37 centers data centers are rapidly growing in recent years and uh this growth is expected to continue it means existing
0:45 network operators and architects will have to do more with less our goal today is to offer a solution
0:51 for your modern data center challenges so that you don't have to make trade-offs between agility and
0:57 reliability uh deal efficiently with operational complexity and reduce constraints
1:03 so that you can make your technology choices without without constraints we have two more upcoming sessions
1:10 one focused on day two plus operations and another one on apis and automation
1:16 um uh we would like it to be more interactive uh so feel free to put comments and
1:23 questions in in the chat uh we'll try to get through as many questions as possible towards the end
1:29 um and and just to make it easier for us to deal with the questions just maybe prefix it with a queue or something uh
1:36 so that we can we can easily find it through the chat but uh definitely comment uh as you as we go along let's
1:42 jump right in quickly on what we plan to cover today uh we will go over the needs
1:48 for a modern data center and then how evpn addresses them uh we'll talk about uh essential
1:55 characteristics of a fabric management solution like what you need to look into a solution when when you're deciding to
2:02 go for a fabric management solution um and then we'll have jeff go over
2:08 you know how to operate an evpn fabric uh using our intent based approach so
2:13 first let's talk about you know modern data centers obviously hyperscalers uh have set a goal standard for modern data
2:19 centers and looking at that looking at the success they have
2:25 everyone wants to build a reliable and efficient and scalable data center like amazon or google right
2:31 however uh we don't operate on the same ground most of the organizations building data centers face unique challenges right uh
2:39 they need to build a modern data center but at the same time they need to support legacy applications uh that may
2:44 require layer to stretch uh while their modern application is talking on ip right so you need a a reliable and
2:52 efficient infrastructure that can support both layer 2 and layer 3. now when you're supporting these layer 2
2:59 stretches right you want to be able to have any vm or any host in any rack you don't
3:05 want to be reserving uh those rack spaces for you know to be on the same subnet uh that means that you wanted to
3:12 be on any rack or anywhere you wanted to right there's also a need uh for having
3:19 a physical infrastructure shared among like you know ports or or applications
3:25 that would sit on the same hardware but at the same time they cannot talk to each other uh they need to coexist uh
3:31 but you may want to isolate it using like vrf like construct or you
3:36 uh want to have some of those flows directed through the firewall um and and that way you can have like that secure
3:42 communication going through if that's not enough uh we actually have
3:47 modern infrastructure going uh using microservices and virtual machines uh
3:53 they add a unique challenge to the network uh there is a constant change in ips and mac addresses that is going on
4:00 in your backend infrastructure that is outside of your networking element and that means that your network has to
4:06 now react to those changes and adapt to those changes without making any configuration changes
4:12 on the network and all these things need to happen on you know a simple ip forwarding
4:18 infrastructure uh that is affordable um and uh you know you want to be able to use
4:24 like you know simple ip forwarding hardware uh wherever possible like you know spine super spine or core of the
4:30 network while your edge of your network is doing intelligence uh things like you know the the the things are described
4:35 above uh this is not a complete list uh but i just try to highlight you know some common scenarios uh if you have
4:42 seen any other challenges or if you want to share something that you know you you are running into uh please feel free to
4:48 put it in the chat and then you know we'll we'll try to get to it uh towards the end
4:54 so while we look at the challenges right um i i think we are in luck because
4:59 uh evpn offers an a standard-based and interoperable solution for some of the
5:04 challenges that i highlighted uh we can just talk along about evpn uh but let's
5:10 quickly see how uh it solves the problem we discussed earlier right so first
5:15 it uses a bgp protocol for signaling bgp as we all know um has you know proven
5:22 over time uh it can catch carry large scale like internet scale or even bigger uh in some service provider network um
5:29 so it is scalable and it will meet your scalability needs uh while bgp is doing it uh we also
5:36 talked about you know being able to do layer two and layer three extensions uh evpn is able to do it uh evpn is able to
5:43 offer you both little l2 and l3 extensions using the same evp and vxlan technology
5:49 uh with bgp now because signaling is happening uh in in bgp
5:54 you don't have worry about flooding like you know you have to worry about in a spanning tree network uh you get your
5:59 traffic low providence built in um and with all that you know characteristics now you can scale better right you can
6:06 you can predict your scale as well and not worry about loops and things like that in production
6:11 uh and beauty of evpn is it comes with a lot of things built in that in past
6:17 needed their own protocol so for example right you get all active multipath now you don't have to block
6:23 ports and and then worry about losing you know ports in your steady state you can use
6:28 all your links and do multi-path and then forward traffics and all links um esi lag uh which basically offers you
6:35 multi-homing not only two two routers or two switches it can do more uh it comes built-in with evpn
6:42 and uh in past you would need you know it eliminates the need for proprietary
6:48 mechanisms like nc lag or mlag now it just happen in an interoperable way with evpn um and i just want to also
6:56 add that it eliminates the need for a chatier vrrp protocol now you can do simply uh
7:02 uni using unicast gateway and then you now don't need vrp across the network uh so evpn just had like you know some of
7:09 these some of these things is just built in uh and it also meets your requirement of
7:15 traffic isolation now you can use l3 vpn like isolation using you know same bgp route target communities
7:22 and it's very easy to you know forward uh traffic through firewalls uh using
7:27 the same mechanism so you get your secured communication and uh using a vxlan overlay which is
7:34 you know simple ip udp private i ip udp packet you can now actually use it
7:41 on on simple ip forwarding infrastructure we can where you can like spines or cores um and then your
7:46 intelligence lies on your edge switches that you know take care of all the evpn functionality uh so
7:53 overall i mean evpn i think is a pretty good your go go-to solution for for the requirements that
7:59 we talked about uh in in a modern data center again if you have any other challenges
8:05 that you know you you think that evpn can solve for you or you have or not able to solve
8:11 please feel free to add it in the chat so we talked about evpn how it elegantly
8:17 addresses your complex requirements but you still need to manage your resources and logic for those complex
8:22 requirements right you still need to ensure the network is operating uh with all those complex requirements it's
8:28 doing intended things and then uh you know your maintenances are smooth and the network if something fails you you
8:34 kind of know things uh the way they are so i i think you all will agree that it's
8:40 uh very difficult if not impossible to do it manually uh but i would also like to say that uh traditional automation um
8:48 will also not be able to cope up with it you actually and we strongly re we strongly believe
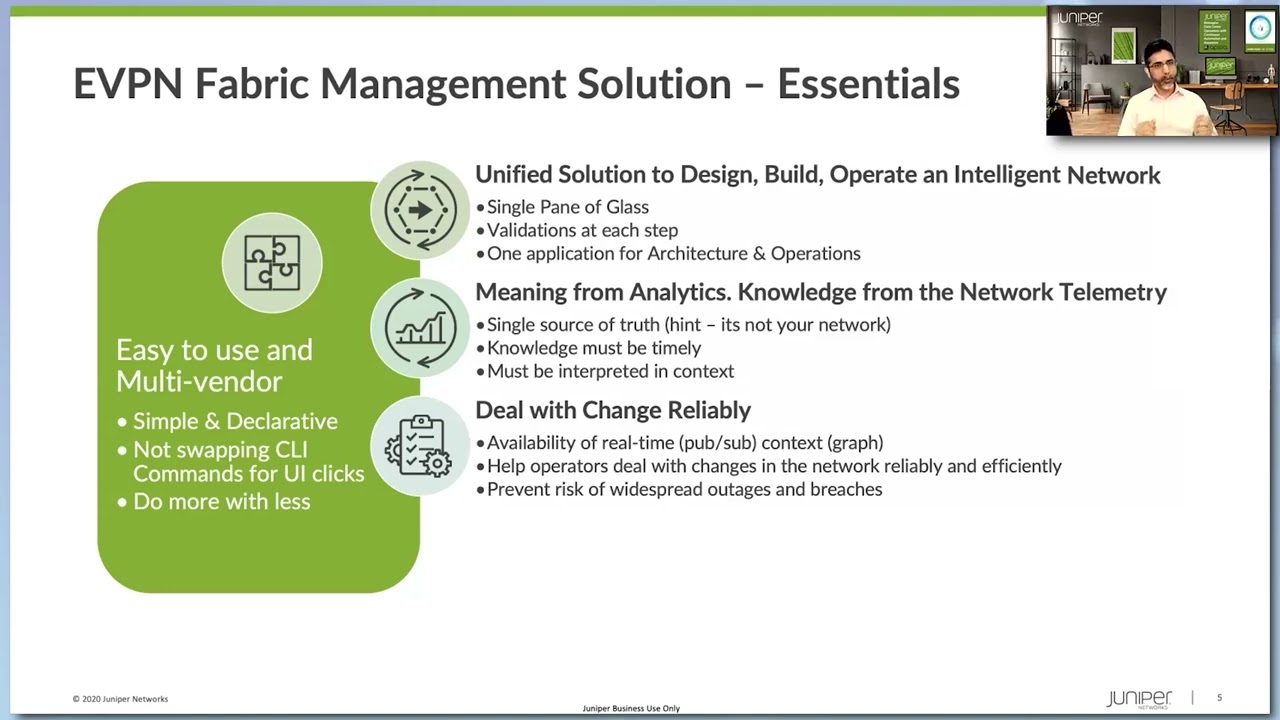
8:54 that you need a sophisticated fabric management solution to manage your uh modern evpn uh data center uh let's look
9:01 at some of the essential things that you know you need to look for right whether you're building at home on your own or you're buying off the
9:08 shelf uh there are certain things you need to look at uh in an evp and fabric management solutions so first and
9:14 foremost right it needs to be easy to use uh i i think there's be no disagreement on that um and it needs
9:20 to be multi-vendor you shouldn't be logged into a given vendor uh when you are you know building uh building a
9:26 management solution um you should be able to simply you know declare or show your intent that hey
9:33 this is what i intend to do with a vpn should go from here to here all these hosts should be
9:39 allowed to talk to that host and the tool itself needs to be able to figure out uh you know what
9:44 configuration goes there depending on the vendor uh what best practices needs to be included in
9:51 that the tool should be able to do all that and you shouldn't be burdened with uh figuring out uh you know the
9:56 configuration and things like that um and uh i think the main thing is you shouldn't
10:02 be like looking at something that just slaps cli configurations that would manually you would do it um and then
10:08 expect it to you know reduce complexity right uh it's one of those examples like you know you
10:13 probably heard when people were asked if people were asked for a faster mode of communication they'll probably ask
10:19 for faster horses but we know that you need to solve it elegantly like a car is we know as we know today is a
10:27 much more elegant solution but it require out of the box thinking so
10:32 that's where you need a tool that takes care of uh you know intricacies of what you need to do it needs to allow you to do more uh
10:40 while you're investing less in worrying about the complexities you just focus on your business needs so that's what's
10:45 like i think the first and foremost thing you need to look at um the next is right while we're operating
10:51 the network i think it's very important that uh we have all aspects or all aspects of your network life cycle
10:57 covered right uh you you need to be able to like you know decide like what you
11:03 want to do then deploy it um and and then and then see it in operational network and then provide that feedback
11:09 loop back if something goes wrong right you're on and it's it's actually doable
11:14 and it's easily and and most effectively done if your architecture and operation teams get the same pane of glass so that
11:22 way they do what they want to do and then they can actually see what is deployed and operated so a unified
11:28 solution uh you need um you need a single pane of glass to do your you know network like life cycle across uh across
11:34 the life of your network uh the next um you want to be able to know like what's going on in the network
11:41 right i mean that's the only way you will be able to figure out what's going on um
11:48 so what what you need is you you need like you know you need to collect
11:53 the right set of information analyze it and then present in a way that's useful for the end user right
12:00 and the thing is like it needs to be on time you don't want to be like you know knowing about something went wrong two
12:05 hours later uh you wanted to be immediate and uh it also needs to give you context
12:11 because the fabric is so big it will be hard for you if you just had sea of errors uh coming at you you need in
12:17 context so that you can take you know precise actions um and all these needs to be done obviously in a modern way um
12:24 so that way you can you know you can query and then get the information you need uh
12:29 the next item is uh dealing with change reliability i i think this is probably the most important aspect of you know
12:37 operating a modern network smoothly um you need to able to have all this information that's going on in the
12:43 network but in order to offer it in context and and and and provide you the root cause in a timely manner uh you
12:50 need to store it in a in a way that's easily you know easy to query uh even though they're like you know these
12:56 relationships that are very complex uh and maybe not even known ahead of time right uh so something like a graph
13:03 database right that allows you to have this complex relationship and then easily query them
13:08 to figure out what's going on um i i think it's crucial uh for for success uh
13:15 that way you get information on time you can you know look at things and then prevent uh risk
13:21 of uh widespread outages and breaches right if you need uh if you get the the problem um right in and in a precise
13:28 manner uh so that's you know that's that's one of the critical aspect but
13:34 last but not least right it needs to be automation friendly we all know that you know most of the
13:40 organization they will operate a large infrastructure on top of the network so they basically preference on uh what
13:47 programming language they use how they you know their workflows are uh and then what's what oss bss systems are there
13:54 right so you want to be able to have that flexibility so apis and simple and usable apis is a must um that way you
14:03 can easily integrate with your existing systems and back against um and then you can do what you want to do and focus on
14:10 your usual business while the two take cares takes care of it so in in summary i would say you know with a
14:16 sophisticated tool uh you actually will get uh to operate in a smooth operation
14:22 or using a sophisticated fabric management tool uh you would get a good experience and then you can grow without
14:28 growing pains right so i think keep in mind all these things that uh when you're looking for a tool
14:35 um i i would say you know put put things in comments if you think there's something else that is more important or
14:41 you know if you think some of these are not applicable to you uh but after establishing that i think i'll
14:46 hand it over to jeff uh so that he can you know walk through a solution that that we can offer that would not only
14:53 meet but exceed you know some of these expectations we we have for for the tool so jeff i'm going to pass it on to you
15:00 great thanks marcia i'm going to skip the slides that i was going to present uh because i think majid did a great job
15:08 of of of really summarizing uh both the benefits of uh
15:16 vxlan evpn and also the challenges and and the major challenge is that it's
15:22 very complex to operate um uh uh manually uh or even with some homegrown
15:31 uh uh automation applications and so what i'm showing here hopefully it's uh uh my
15:38 screen is is showing is um and uh a juniper abstra uh
15:45 blueprint of uh working um well in this case not a working network but a network
15:51 and i've got a couple of different blueprints running in a couple of different labs
15:56 that i want to talk about and because we're really talking about operations and day two
16:03 [Music] complexities i won't spend more than just a couple of minutes
16:09 talking about really how this particular
16:16 blueprint is assembled but but i do want to say a little bit about it you know because i
16:21 think it's important to say okay how did i get to this point and what you can see here is is a
16:28 fairly simple uh data center topology with two spines
16:33 and six racks uh there's five server racks and in this you can see
16:39 we say there's 24 generics basically these are 24 servers
16:45 and i created this pretty quickly and the other rack here is a border leaf rack and by the way there are uh
16:52 redundant top of rack switches in each one uh this border leaf
16:58 provides outside access the two generics here are firewalls and and there's also three access
17:05 switches which just extend extends access out what's important to note
17:12 about this is that when i built this i built it by specifying just logical devices uh an
17:20 abstraction of the switches i want um so you know i specify for my spine
17:26 switches i want a certain number of ports and a certain number of port speeds for my top of rack leaf switches
17:35 i also specify i need a certain number of ports and a certain number of port
17:41 speeds and then i create a template that specifies how all of
17:48 this ties together at no point in there at that stage do i actually make a
17:54 selection of what specific vendors i'm using
18:01 i only do that after i know that that the blueprint that i want to use is actually working
18:07 and you can see in this diagram with everything put together in a blueprint
18:13 i also specify what resources i'm going to use i specify
18:19 pools of asn numbers loopback ip addresses link ip addresses
18:25 i do that in a separate menu excuse me
18:32 that then tells appstra this is the pool of uh resources i want to use for this
18:39 specific data center and i don't have to make any choices beyond that appstore will take care of
18:46 managing that if you uh have an outside resource management
18:54 platform um like ipam obviously uh we can connect to your ipin
19:02 ipam system through apis to further manage those resources
19:07 only when i have all of that put together would i actually
19:14 decide what vendors i want to use in this particular case
19:19 for my spines you can see here that and i'm doing this specifically to show
19:25 our uh vendor independence it's only after um i specify you know what my topology
19:34 looks like to answer my specific data center needs
19:39 do i look to see what vendors will meet that in this
19:45 particular case on spine1 i have a cisco nx os switch on spine 2 i'm running
19:51 arista for my leaves i have a mixture
19:56 of cisco and arista switches running here and for these three access switches i'm
20:03 actually using juniper exes but uh but uh so those are already selected but
20:11 you can see that you know for my spine switch you know i specified
20:17 uh for my spines i want 32 40 gig links
20:22 and i get a list of the various switches that meet that requirement
20:31 which includes the cisco that i chose and the arista that i chose so
20:36 so i'm selecting my vendors according to um to my specifications there
20:43 um so that's just i there's a lot more that i could oh maybe one thing that i should
20:49 mention is um once i have my vendors selected um i can actually uh get
20:57 a cabling map and appsera will take care of actually
21:02 telling me um what ports to cable to what ports and i can
21:10 not only get that within app store i can export that um actually i intended to
21:18 let's try that again i can export that as uh csv uh which will fit into any uh excel
21:26 uh i'm sorry uh any spreadsheet uh so for example here i'm using uh google
21:33 um google chrome and um i can
21:41 it should there it is uh it took a minute for for that to process i can i
21:46 can print out an actual cabling map uh that my data
21:51 center uh uh technicians can take and and when they
21:57 rack up the specific devices it tells them what interface
22:03 to connect to what interface and this is a verified cabling map
22:09 we can also do things like affinity checks so they're so no two
22:14 connections are in a common failure domain or you know sharing a transceiver
22:20 or uh anything like that so um so all of that is verified ahead of
22:26 time but what's really important is
22:31 let me get this so there we go is the because we're emphasizing operations
22:38 here what's important for operations are three parts it's the day-to-day
22:44 uh configuration changes that you make in your in your network it's
22:50 the day-to-day information collection that you need to make about your network
22:56 and when there are anomalies in your network you need to be able to quickly resolve those anomalies and all three of
23:03 those things are our day two operations so just to show a
23:09 little bit of that uh going back to i've got my physical view here
23:17 and this topology that i created but then i want to
23:22 just as an example of of day two operations
23:27 i want to start creating some virtual objects within this network so
23:34 the first thing i might want to do is create a couple of routing zones
23:40 and one of the things maybe i should have
23:45 kept a couple of slides one of the things i do want to show you
23:50 just from a slide here is this is from an another lab that i
23:55 put together and i've got a sonic configuration or a snippet of a sonic configuration a snippet of index os
24:02 and a snippet of eos and the question that i posed up here is well do all of
24:07 these things do the same thing uh the answer is yes and um and i'm not sure
24:13 how well that shows on your screens but what you can tell in here is that these are all
24:21 configurations for a vrf named vrf blue
24:26 and but what is significant is when you look across these they are very
24:32 different configurations uh in appearance and the
24:37 the uh the thing is they do actually all do the same thing these are all abstract
24:44 generated configurations and that's the important point to make here uh as i as
24:49 i go into this piece um so let's say on routing zones
24:54 and you saw that configuration for a routing zone let's create one or two and maybe i'll
25:01 call uh i'll create a routing zone called blue
25:06 i could if i want uh specify my vlan ids to be used here my vni's
25:12 i set my routing policy and i could choose my import and out uh
25:18 export route targets uh very specific uh and very important for
25:23 uh vxlan evpn but i'm not going to do any of that all
25:28 i'm going to do is give it a name and i'm going to let abster take care of all the rest of it so i'll hit create there
25:34 um and i'm going to create one more just for the uh fun of it let's call this one
25:41 green and the same thing i'll let abstra take care of all the other choices in there
25:47 and here you can see that blue is created and green will pop up in a second
25:52 and it will also figure out the route targets uh not quite there yet
25:58 and you'll specify uh the resources you want to use so in this
26:04 case i'm going to say for my loopback ips i've got a resource that i've called data center one loopbacks
26:11 i'll use that for green i also specify my lootbacks
26:18 and and for my l3 vnis i have a pool of vni's that i've
26:26 specified for data center one and i select all of those
26:32 and uh everything should go green and uh and we're ready to go there and you can
26:38 see that actually took a little longer than i expected but uh but you can see that appstra
26:43 has uh specified my route targets my vlan ids and my vnis for those three
26:51 vrfs what we call routing zones are just vrf's so then i can specify
26:58 uh some virtual networks and i'll just do a couple here but the point here is showing how fast the
27:03 operations go so well i have a via let's call a vxlan and um just to be a
27:10 little whimsical there i'm going to call it stan and i'm going to put that in that blue routing zone that i just created that
27:17 blue vrf i'll let um [Music] again abstra take care of making all the
27:24 choices about vnis i can specify that i want the same vlan
27:29 id on all leaves i want dhcp enabled
27:35 and i want to tag that and then i can specify uh what racks i want that
27:43 vtep to appear on and i'll create that and i'm kind of doing this randomly so
27:50 um it'll be interesting to see if i managed to do this with no mistakes one more vxlan just to show and we'll
27:56 call this one ollie um again let's put that in the green routing zone that we just created
28:04 uh specify again that it's tagged and let's say that's going to appear on um
28:12 on this on the border leaf and on
28:17 these first three server racks and again i'm just quickly making choices there
28:24 and uh then i have to specify
28:29 my uh svis i've got an svi pool here so i'm just telling i'm not actually
28:34 specifying any of this i'm just telling uh abstra the pools that i've uh created ahead of
28:42 time select your svis out of that pool
28:48 and so vni's and we'll get a little spinny wheel here for a second as things
28:53 process i specify that i specify my vtep
29:00 ips and at this point everything should go
29:06 green and let's see it will quickly go there
29:14 it goes um what's happening in the background when you see that is that
29:19 uh appser is actually going through the it's creating configurations and then
29:25 it's going through and verifying all of those
29:30 configurations so if there's anything that the validators that we have built
29:35 in uh don't like they'll inform you of that and um and
29:41 usually when i do these very random things i manage to make some kind of a mistake that a validator will come back
29:47 and say hey there's a problem there in this particular case it didn't uh but
29:52 one of the things uh i do want to show you here is that now with this uh with
29:58 this configuration i can for example uh go to a specific
30:06 node in this case i'm going to go to leaf one of server rack one and what i can see
30:14 here is that this is an incremental configuration this is what
30:20 in those very few clicks that i made uh abstract created and i can see just by a
30:26 quick glance if you're familiar with arista eos you'll know that this is an eos
30:32 configuration and you can see here's my vrf blue that i created here's green
30:38 and all of the other information i need under there is created for me so my
30:43 vlans are there uh all of my bgp configuration is there
30:49 and just to show you very quickly if i for example
30:54 uh switch to borderleaf one here if i look at my incremental config
31:01 there you can see very quickly that's an nx os configuration abstra knows that uh that
31:07 that border leaf is in xos so i have that all configured all of my details
31:14 are there they're all uh validated and so i know that's going to work and i don't have to go through any of the
31:23 minutia of actually physically creating this
31:28 configuration and then labbing up the configuration and then validating it manually it's all done for me and um and
31:37 you know and once i have verified everything i would go to the committed tab hit commit and that commits all of
31:45 my changes uh if you're familiar with juniper junos you certainly are familiar with
31:51 the idea of a candidate config doing a commit and then having an active
31:56 config and so that is a the uh day two operations as
32:02 far as just the day-to-day kinds of things you would do of creating new vrf's creating uh
32:09 virtual networks and uh and so forth and i'm going to switch this is a different
32:16 actually a different blueprint i one thing i should say about this blueprint um that i'm
32:22 running actually in in um a server in my home office here is that at this
32:29 point i don't actually have any of these devices i specified uh that i want you
32:35 know certain devices to be arista certain devices to be cisco um on here and you know and some juniper
32:43 devices i don't have any of those installed yet i've created all of that
32:48 um specification in uh preparation for actually
32:54 installing the devices i have a cable map that i can now uh connect all my devices together i've got all of my uh
33:02 logical configurations done and when i bring the devices up under appstore control i then just push all of
33:09 that out to the devices this particular uh
33:15 blueprint here it's a little bit simpler blueprint with two spines and two racks
33:20 one with two copper rack leaves one with a single top of rack leaf and in this case these
33:27 are all juniper devices and there is uh junos running underneath this and
33:33 as a result you can see that there's some differences uh at the top here um
33:39 you know where on my other blueprint dashboard analytics and active actually said in a
33:45 they're green here what i wanted to show you here very quickly is uh if i go to analytics
33:54 and interestingly enough there are three anomalies it says that i have uh some systems with high cpu
34:01 utilization um that actually surprises me i'm not sure why that's going on in in my lab but uh
34:07 um but nevertheless uh it's it's a good thing to go uh to to show that that uh
34:13 appstra quickly shows you those kinds of anomalies uh but another part of what
34:21 i would want to do as part of my day-to-day operations is
34:26 gather information about my network so for example if i go
34:31 to device traffic i can very quickly uh display and there's
34:37 not really much going on in this network so so pretty much everything shows zero packets per second
34:44 but very quickly i can i can see what's going on in my network in terms
34:50 of of traffic bandwidth utilization
34:56 another thing that i could do and by the way you do all this by creating probes
35:01 maybe i need to see some information about critical services and so i can very quickly select a probe
35:09 on critical services and then this is something i did ahead of time on
35:14 all of my servers i specified uh what kinds of services are running on
35:23 those services so in this particular case i might want to say that i want to know what my critical services are doing
35:29 for my app development and maybe for i have a test
35:36 network and maybe for finance
35:41 on those particular applications i want to create a probe and it takes a minute but but
35:49 what i have now again not really anything going on in the network is very quickly i can look
35:56 and and see for those critical services that are running in my network what my uh
36:03 bandwidth utilization is uh uh you know where they're running what interfaces they're running on and
36:10 so forth and there are a lot of uh variables that i can set to query
36:18 uh what's going on in that network there's also a lot of variables about how to
36:24 uh query uh the network the last thing i want to show because i know we're quickly running out of time
36:30 here is uh is uh within analytics and also on the
36:36 dashboard um i could very quickly see what's going on
36:41 in my network so when there are anomalies and interestingly enough let's just click on that anomaly uh because
36:47 i'm not sure what what's going on there oh you can see there was uh in this particular case for device system health
36:55 it's saying that uh that i have some cpu utilization that's running beyond
37:02 uh and it's on these specific devices actually that's all my devices
37:07 i'm running at 27 and i had a threshold saying let me know
37:12 um when my cpu utilization gets beyond a certain point
37:18 but with a longer demonstration what i normally like to do here
37:25 is sort of go in the background and create a problem on the network and then show
37:30 how quickly i can go through uh and troubleshoot that problem and literally resolve the problem in
37:38 in just a minute or two um but uh given our time limitations
37:44 here uh i'm gonna stop at this point um maybe one thing else to show because
37:50 this is something that uh maj had uh pointed out is uh
37:56 our theme here is managing complexity and if i actually again you can see this
38:02 very simple network that we have here uh in the background abstra is tracking this
38:08 network uh in a graph model and i could actually look at that graph model and
38:14 again you know just showing that this is a extremely simple
38:21 uh network and yet uh here's the the graph model
38:27 for uh for actually tracking that network and you can see that this is something that's that's tremendously
38:33 complex here and so this is something that's all being worked in the background and would be almost impossible uh to
38:41 completely manage if you're trying to do all this manually uh so i did want to point that
38:47 out because i feel like you know there's a lot that i could say about this graph model
38:52 but you know there's there's a lot i could say here in terms of uh managing complexity but i wanted to at least
38:59 show that to you and at that point uh much it i'm going to throw it back to you
39:05 and maybe at this point we want to open up for questions
39:12 yep no sure jeff i think uh we we can certainly open up for a question real quick i think in summary i want to say
39:18 like uh you know for our quick discussion today uh we we kind of highlighted that you know evpn vxlan uh
39:26 is is a technology that offers you an efficient and scalable l2 and l3 connectivity uh
39:33 but in order to manage your fabric right you need a sophisticated solution um and
39:38 then just not any solution but you would need a unified solution uh for seamless
39:45 automation from day zero to date day two so that you know your architects and
39:50 operations guys can see through the same pane of class right and based on you know what jeff showed you
39:56 and then the things that we talked about uh i think you uh we'll all agree that you know juniper abstra uh actually does
40:04 uh meet all the requirements of a of an effective fabric management solution and then does it in a way uh that you
40:12 know it helps you do uh more with less and then grow without growing pains
40:18 and then in addition to that if you want to know more or or learn more you actually actually have free resources on
40:24 juniper website uh we have a training portal uh we also have virtual labs um
40:29 and then there's a fantastic youtube list where you can actually see uh videos like this on you know how how
40:36 abstract can help you with your fabric management uh so i'll i'll conclude
40:41 with that and last thing is that we're actually going to have more lightning sessions like this about how abstract
40:47 can help your day 2 operations or how it can help integrate with your existing fabric
40:52 uh so please uh you know tune in to those those as well uh so jeff before we close any any closing comments from you
41:00 no i uh uh other than just saying you know if you'd if you'd like to see a more extensive demonstration of abstract
41:07 i'm always available to do that definitely thank you thank you jeff and
41:13 thanks for joining uh folks we'll look forward to talk to you more
41:19 [Music] you